Erica Kastner
Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.
MANAGED IT SERVICES | 4 MIN READ
Maximizing productivity and efficiency is a business goal that is always top-of-mind for companies. Businesses looking to achieve this may think of ways to streamline their sales process or supply chain. However, many.
Managed IT Services,
cyber security
Read More
CYBER SECURITY | 5 MIN READ
Expanding your company to multiple offices is an exciting development. When building new branches, you might not consider the necessary steps to set up your network to securely handle employees from multiple branches working.
cyber security best practices,
cyber security solutions,
cybersecurity,
small business cyber security
Read More
MANAGED IT SERVICES | 5 MIN READ
If you're reading this article, then deep down you probably already know that it's time to cut ties with your MSP. If you're still on the fence, you might want to know what factors to keep in mind when making the decision.
Managed IT Services,
MSP Questions,
Managed Services Questions
Read More
CYBER SECURITY | 6 MIN READ
In some ways, maintaining the network security of a regular office can be easier than managing a remote office. As a Managed Service Provider, we aim to use our cyber security expertise to educate our audience about how to.
cyber security
Read More
CYBER SECURITY | 9 MIN READ
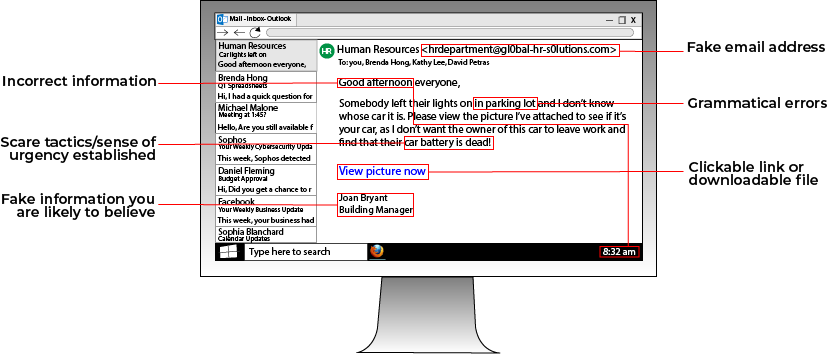
Varying the passwords you use for everything from your email account to your company's HR database is a great first step at protecting your data, but what happens when you have so many passwords that you begin to lose track of.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
MANAGED IT SERVICES | 6 MIN READ
When shopping for managed IT services, you may come across the terms NOC and help desk. While they sound similar, nuanced differences between the two exist. Based on your business' needs, you may find that one is probably.
Managed IT Services,
Network Protection Atlanta,
Network Protection,
cyber security best practices,
cyber security solutions,
Managed IT Services Atlanta
Read More
CYBER SECURITY | 13 MIN READ
If your company is looking to transition your office to work remotely, you might be wondering how to make that transition, especially when your office currently has little to no remote workers. From a technical perspective,.
cyber security
Read More
DARK WEB | 4 MIN READ
A place rumored to be full of illicit activity, the dark web's mystery intrigues many.Because the dark web is an in-tangible concept hidden away in the corners of the Internet, i t can be hardfor one to even grasp what the dark.
dark web,
cyber security
Read More
CYBER SECURITY | 5.5 MIN READ
In our rapidly changing world, it's hard to predict what somebody might have for breakfast tomorrow, let alone how ransomware will change in the coming years. Read more to learn about developing ransomware trends that could.
cybersecurity,
ransomware and phishing
Read More
CYBER SECURITY | 10.5 MIN READ
Major news outlets, from CNN to Forbes to the New York Times, have been reporting recently on the growing and shifting threat of ransomware. Just last week, the New York Times reported on the continued growth of ransomware.
cyber security best practices,
cybersecurity,
small business cyber security solutions,
ransomware and phishing
Read More
DARK WEB | 10.5 MIN READ
Though the dark web seems like an invention of the new millennium, its history dates back farther than one might think. A few pioneers built the dark web into what it is today, a hidden underbelly of the Internet with content.
dark web
Read More
CYBER SECURITY | 7 MIN READ
The healthcare industry must follow strict protocol to remain compliant with HIPAA. Because many organizations within the industry store private information like patient files and financial information, the industry as a whole.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 7 MIN READ
If you're currently in the market for a managed services provider, you might have seen or will come across a contract spelling out your services agreement. Managed IT services contracts can come with terms that might confuse.
Managed IT Services,
cybersecurity,
Managed Services Questions,
cyber security
Read More
CYBER SECURITY | 8 MIN READ
The legal industry ranks among the healthcare and finance sectors as one of the most targeted industries for cyber attacks. The common thread that makes them attractive targets is the personal information that they store and.
small business cyber security,
small business cyber security solutions,
cyber security
Read More
CYBER SECURITY | 7.5 MIN READ
As a Managed Service Provider, our clients ask us about the benefits of cloud versus on-premise security all the time. Data security is becoming more and more crucial for businesses as cyber attacks are on the rise, which.
cyber security solutions for small business,
small business cyber security,
small business cyber security solutions,
cyber security
Read More
RANSOMWARE | 12 MIN READ
Ransomware attacks pose one of the biggest security threats to both individuals and businesses alike, showing no signs of slowing down as hackers grow increasingly tech-savvy and Ransomware-as-a-Service (RaaS) is making it easier.
ransomware and phishing
Read More
RANSOMWARE | 6 MIN READ
Ransomware is the modern day mobster, allowing hackers to shake innocent victims down for their money with no remorse. You've probably seen major news outlets covering stories about it for years, but what exactly is ransomware?.
what is ransomware,
ransomware and phishing
Read More