FACIAL RECOGNITION | 5 MIN READ
As facial recognition becomes more widely used in businesses and government entities alike, and especially due to COVID-19 causing widespread mask wearing, many are wondering if this technology can correctly identify individuals wearing a mask. Keep reading to find out if facial recognition can identify you when you're wearing a mask as well as if facial recognition can be fooled.
Not enough time? Jump to:
Can You Be Detected With a Mask?
How Does Facial Recognition Work?
Can Facial Recognition Be Fooled?
Cyber Criminals are Exploiting Technology
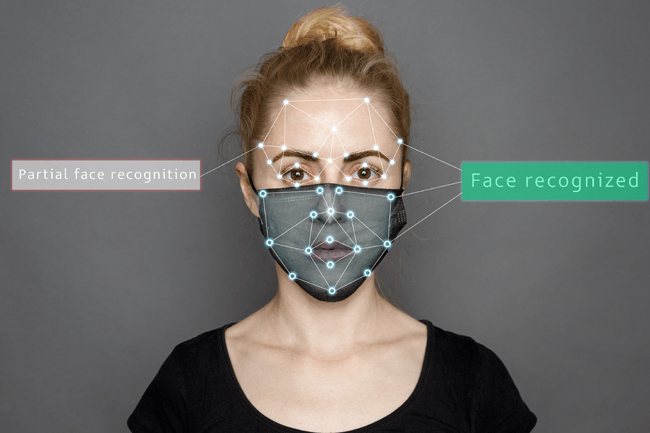
Can You Be Detected with a Mask?
For the most part, yes, one can be identified by facial recognition even when wearing a mask. This is because masks tend to leave the eyes, which are a crucial data point that these system use to identify an individual, open.
For those looking to wear masks in public to stay safe during the COVID-19 pandemic, this is a welcome answer. However, for those looking to trick a facial recognition system, they may have to employ other methods.
Temperature scanners are a good example of facial recognition technology that can identify faces even when an individual is wearing a mask.
Temperature scanning kiosks use a combination of facial recognition and infra red technology to identify an individual, assess their temperature through their forehead, and store this data for tracking purposes.
These kiosks are best suited for businesses who wish to monitor visitor traffic as well as mitigate the spread of potentially infectious conditions.
To use one of these kiosks, an individual must step within the target range, which is usually about 1-3 feet. Using infra red technology, the kiosk will scan the individual’s forehead and take their temperature.
If an individual has a temperature higher than the allowed threshold, they can be pulled aside for additional screening.
With some brands, user profiles can be created to recognize repeat visitors and historically track their temperatures. This is useful in the event of having to contact trace an individual who becomes sick with a contagious condition.
RELATED: Temperature Scanners for Businesses [Types + Pricing]
How Does Facial Recognition Work?

Facial recognition technology uses biometrics to map a user's facial features from a photograph or video. Biometrics are biological measurements such as one's eyes or face shape that can be used to uniquely identify an individual.
To build this map, also known as a facial signature, facial recognition technology notes a number of unique characteristics on one's face, with key factors including the distance between one's eyes and the distance from one's forehead to their chin.
A facial signature comprised of a complex mathematical formula is then created using this data. After mapping an individual's face, this technology then compares this information with a database of known faces to find a match. Some databases can contain hundreds of millions of photos or more.
To improve a facial recognition system's accuracy, developers tend to rely on machine learning, a subfield of artificial intelligence. Machine learning involves computers teaching themselves tasks to independently improve their skills sets.
When it comes to improving the accuracy of a facial recognition system, machine learning is used to reward the computer for correct facial identifications and penalizing it for mis-identifications.
In this environment, over time, the system learns to distinguish human faces from other objects, and then how to accurately distinguish one face from another. To distinguish one face from another, the system uses a complex variety of anatomical features previously described, such as one's eyes or the distance between one's eyes.
Can Facial Recognition Be Fooled?
While facial recognition technology is consistently improving, it still has a ways to go before it's infallible.
There have been instances when someone has been able to fool it by wearing a disguise, holding up a picture on their phone, or, in a particularly complex scenario, wearing a printed lifelike mask resembling someone else's face.
There are two main ways in which people have been able to fool facial recognition systems: through obstruction of one's face or by confusing the system into mis-identifying a face.
Obstruction
By cleverly covering one's face, an individual may be able to trick a facial recognition system into simply thinking that they're a non-human object passing through.
Many try to thwart these systems by simply wearing a mask or hat. However, the main areas that a facial recognition system scans are the eyes, mouth, and nose. By simply wearing a mask or hat, some of these crucial facial points are still exposed, which means that a system can still identify an individual.
Some people go to extreme lengths to ensure that their entire face, including the mouth, nose, and eyes, are covered.
While wearing a covering like this may effectively trick the system, it is also conspicuous, which makes these types of tricksters easy to identify, especially when security personnel are manning facial recognition checkpoints.
Confusion
A more advanced way of fooling a facial recognition system involves the strategic application of makeup, camouflage, or the use of lasers, as seen in the Hong Kong protests.
Strategically applying makeup that either covers the main facial recognition points or strategically deflects light off certain parts of the face can scramble a facial recognition system by making it identify an individual as something else.
However, the flaw in this method is that there are different types of facial recognition software, so to effectively trick a system, a user must know what type of system is utilized in the area they're trying to gain access to.
Special camouflaged material such as scarves and earrings can be worn inconspicuously to confuse a facial recognition system.
Designers have created camouflage with a pattern that a computer will register as a bunch of faces. When a computer scans an individual wearing this camouflage, it may become overwhelmed by the sheer number of faces, which can allow said individual to exploit the system.
By pointing handheld lasers at the camera on a facial recognition system, one can disable the sensors in the camera, effectively stopping the system from scanning.
How to Stop Tricksters in Their Tracks
Businesses can minimize the odds that a user fools facial recognition by requiring visitors to not wear material that shields their face, at the very least when passing through facial recognition checkpoints.
Having security personnel at checkpoints can also ensure that suspicious individuals trying to trick the system are quickly identified. Facial recognition tricksters can also be thwarted by requiring multiple verifications at a checkpoint.
For instance, at an airport, if one's face has to be scanned before boarding a plane, maybe they also have to provide a form of identification such as a driver's license, or a date of birth.
Cyber Criminals are Exploiting Technology

While cyber criminals are already looking for ways to trick facial recognition systems for their own benefit, they are also exploiting other cutting-edge technology to carry out social engineering attacks.
Social engineering relies on deception to trick a victim into clicking a link or downloading a file that then lets a hacker steal personal information or hack an account.
Keep reading to learn about other modern forms of technology that cyber criminals are exploiting for their own gain.
Deepfakes
Deepfake technology is a growing concern in the cyber security industry. It involves a combination of machine learning and artificial intelligence to edit a photo, video, or voice clip with malevolent intent. This media is then used to trick victims into handing over personal information.
The trend, which first started gaining ground in 2017, started off as a way for people to edit celebrities and other people's faces onto sexually explicit videos so it looks like those people were the ones in the video.
With the 2020 presidential election coming up, some are concerned that deepfakes can be used to manipulate political images and videos to the editor's liking. This growing trend makes cyber security experts worry about how deepfakes can be used to persuade victims into handing over their personal information.
For instance, a victim could be emailed a video that looks like it's from their IT manager asking for their account login for routine maintenance. Or, a victim could be emailed a link to join a remote conference with a co-worker or client, but in reality the person they're talking to and discussing personal information with is an edited face.
Deepfake social engineering attacks are already being reported − the Wall Street Journal reported on a CEO scammed out of a quarter of a million dollars over a voice scam.
While the future of how deepfakes will be used is uncertain, the possibility is there for the technology to be used to carry out social engineering attacks and steal victims' personal information.
SIM Swapping
Enabling two-factor authentication whenever possible is one of the top-rated cyber security tips from leading industry experts. However, a growing trend called "SIM swapping" is rendering this security tactic useless.
SIM swapping is a social engineering tactic that gains access to a victim's accounts that are protected by two-factor authentication by tricking them into providing the one-time passcode sent to their phone. Once the passcode is given, the attacker can use it to their advantage to receive all texts and calls intended for the victim.
This allows the attacker to receive all passwords for account logins and break into a victim's personal accounts. While you should still enable two-factor authentication whenever possible, be extra diligent about paying attention to the websites you use to log into personal accounts.
RELATED: Social Engineering Trends in 2020
Facial recognition technology is so advanced that it can typically detect you even when you're wearing a mask. Though it isn't perfect, research and development will continue to improve its accuracy.
Its applications for society are endless, and over the coming years, we will start to see it further and further ingrained into everyday life.
Follow our blog to learn more about the latest cyber security topics!
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

