
CYBER SECURITY | 6 MIN READ
Spam, sometimes mistaken for the packaged meat product SPAM, is an online nuisance that you have likely experienced before. While we all think we know, in general, what spam is, fully understanding it is key in knowing how to avoid it. Keep reading to learn what spam control is and what steps you can take to secure your inbox.
Not enough time? Jump to:
Corporate Spam Filtering Solutions
Other Ways to Reduce Spam Emails
What is Spam?

Spam emails are any kind of unwanted and unsolicited email that are usually sent with the intent of selling a product or service. For instance, you could receive an email from a company you've never heard of trying to sell you on their "revolutionary new face cream".
These emails are usually sent in bulk batches in an attempt to reach anyone who will listen. Senders hope that by casting a wide net, they will reel in a few interested buyers.
These emails can be a drain on company time when employees have to constantly sift through and delete them to get to actual important emails.
Spam isn't just limited to email though. It can also be found on Internet forums, social media, and more in the form of direct messages and comments.
History of Spam
Spam gets its name from the infamous canned meat product SPAM. Hormel Foods, the maker of SPAM, has previously taken legal action to protect its name, as it wishes to not be synonymous with unwanted email.
According to Hormel branding guidelines, they advise that people refer to their product as "SPAM", and unwanted email as "spam".
The first spam email can be traced back to 1978, when an email ad for a presentation by Digital Equipment Corporation (DEC) was sent over ARPANET, a precursor to what we know as the Internet.
From there, as email popularity grew in the 1990's, spam began to flood the Internet.
How to Control Spam
While many modern email providers have filters built-in that automatically detect and move spam emails to another folder, these filters aren't 100% accurate.
If you're in a position of power at your company, spam senders target you more than average, which means that your already full inbox will likely let through some spam emails, hindering workplace productivity.
Spam can be minimized through the use of email filtering software.
This software analyzes incoming emails for red flags that signal spam or phishing content and then automatically moves them to a separate folder.
Spam filters use multiple criteria to assess an incoming email. They look for common trigger words that signal an unwanted email attempting to sell you something, such as "free" and "earn money".
If the sender sends you an email using your email address instead of your contact name, that could trigger your spam filter, seeing as the sender won't be in your contacts. Senders trying to send you content such as newsletters that you haven't opted into may be flagged as spam.
Additionally, if the sender's IP address has previously been flagged for sending spam, a sender with the same IP address will likely be flagged as well.
Even the content and design of the email itself can trigger a spam filter. Gaudy large fonts or large images are two main layout triggers for spam.
Email filtering software can also be used to monitor for phishing emails.
While all of the above criteria may automatically put an email on a content filter's radar, additional red flags will trigger a phishing filter.
Phishing emails usually include a link or attached document that's filled with malware used to hack your network. Senders who have been flagged for having a history of sending malware may set off a phishing filter.
Emails from unknown senders containing links or attached documents may also set off phishing filters.
Phishing filters will typically move flagged emails to an additional inbox, sometimes labeled as "Other". In this inbox, flagged emails will be put "on hold" until you release, block, or allow it.
If you release an email, then it is sent to your normal inbox to be opened, but in the future you will have to continue approving emails from the sender. If an email is blocked, then the email is rejected and the sender will be now be blocked from sending you future emails.
If an email is permitted, it is delivered to your normal inbox and the sender will automatically be approved to send emails directly to your inbox moving forward.
RELATED: What is Phishing? [Types and Tips to Prevent]
Corporate Spam Filtering Solutions

Mimecast
Mimecast is a diverse solution that goes past simple spam filtering (and also our recommendation!). They also have malware, virus, and phishing filters in place that minimize the threat that these emails can pose to an organization.
Emails from any unverified external senders are kept in a separate inbox "on hold" where they must be manually released, blocked, or permitted before they can be viewed.
If you release an email, it will be moved to your inbox, but future emails from that sender will be placed on hold. Blocked emails are rejected and the sender's email address will be blocked from sending you future emails. Permitted emails are moved to your inbox and future emails from that sender will not be placed on hold.
This minimizes the chances of someone curiously opening an email from an unknown person and clicking a phishing link.
Mimecast also offers email continuity, archiving, and advanced search features.
SolarWinds
SolarWinds' email filtering software blocks spam, viruses, and malware, with the additional option to filter for phishing content. This is useful for organizations looking for an all-encompassing email security solution.
They also have email encryption services that securely store emails in case they're accidentally deleted. Their platform is compatible with a variety of email servers too.
TitanHQ
TitanHQ offers a robust solution to email security. Their spam filters accurately detect and move spam emails before they have a chance to penetrate your inbox, therefore protecting sensitive data from hackers.
Blacklist and whitelist features ensure that non-permitted senders don't continue to harass you with spam emails, while sandbox features let teams safely open suspicious emails to check their contents.
Other Ways to Reduce Spam Emails
Recognize the Signs of a Scam
While enabling email filtering can prevent phishing and scam emails from victimizing you, sometimes, a few sophisticated ones can make their way through.
Email filters are not enough to protect you from being victimized by a scam. You must learn how to recognize the signs of an email scam if you wish to prevent yourself from falling for one.
There are a few common signs that an email may be a scam or phishing attempt. The first step is knowing the difference between a phishing email and a spam email.
A spam email is relatively harmless. While the email may come from an unknown address or look generally abnormal, these types of emails usually are trying to sell you on something. For instance, a spam email could aim to entice you into buying adult content or reading an unwanted newsletter.
On the other hand, a phishing email is designed to trick you into providing personal information that can be used to hack your private accounts and steal money. There are a few red flags that can be used to quickly recognize and stop a phishing scheme in its tracks:
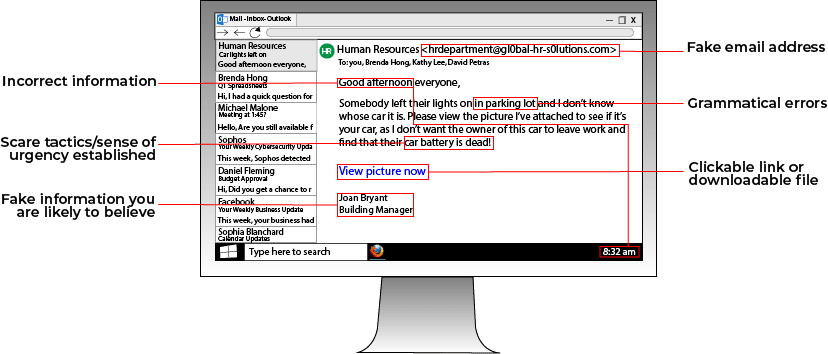
While an email with some of these characteristics won't always be a phishing email, you should automatically be on alert when you notice any of the above signs.
If you're a business, all it takes is one employee falling for a phishing attempt to compromise your entire network. Businesses should hold educational seminars to teach employees about cyber security best practices.
At these seminars, which can take place in person or online, businesses can teach employees about ways to recognize and avoid phishing schemes, create strong passwords, and avoid common cyber threats online.
There are even companies that can conduct phishing tests within an organization. They'll send a fake phishing email to everyone in the company, and then send anyone who falls for the trap to an online cyber security seminar.
Educating employees about cyber security builds a culture of personal accountability within an organization.
Strengthen Your Password Security
A weak password is one of the easiest ways to let a hacker into your personal accounts. A trap that many people fall into is repeating passwords across multiple accounts.
Even if your password is strong, all it takes is a hacker accessing one account associated with that password to grant them access to all related accounts. Limit repeating passwords and refrain from writing them down anywhere when possible.
Although writing down passwords in an Excel spreadsheet or in the Notes app on your phone is convenient and keeps you from having to remember all your logins, this leaves the door open for someone with bad intentions to discover and take advantage of this information.
If you must write down passwords, consider a secure password-storing program. These programs store all your account logins in one secure location and then auto-fill the login forms when you visit an associated website.
If you ever want to view your stored passwords, simply log into the storage program, which is protected by multiple layers of security. When it comes to creating secure passwords, we have a few quick tips that you should keep in mind.
Refrain from including personal information in your passwords that can easily be found online. This includes everything from your birthday to your children's names to your alma mater.
While personal information helps make passwords more memorable, you should use specific information that only you would know. For instance, your password could include the name of your favorite vacation spot from your childhood or your favorite food you ate growing up.
Passphrases are another easy way to make a memorable password that's hard to crack. Passphrases are formed by taking 3-4 random words and stringing them together.
For instance, a passphrase could be "blue frog mountain pyrex". Although this password is easy to read and remember, according to the website How Secure Is My Password, this phrase would take a computer over 4 sextillion years to crack!
Consider Managed IT Services
As a Managed Service Provider (MSP), we understand the challenges that businesses have with securing employee inboxes. MSP's like us can secure both your inbox and your overall network by implementing layered cyber security solution.
With our clients, we start by installing Mimecast to secure their inboxes. From there, we can install a host of other software such as antivirus and anti-ransomware to keep all cyber threats at bay.
RELATED: What are Managed IT Services?
Understandably, organizations wish to avoid spam. Use the solutions laid out in this article to control spam within your organization.
For more IT-related content, follow our blog!
Posted by
Tech Support

