DATA BACKUP | 5 MIN READ
Many businesses know that data backups are an integral aspect of data security. However, the tasks of determining how often to back up data and the best backup protocol can be complex. As a Managed Service Provider, we assist.
cyber security,
BCDR plan,
Data Backup
Read More
CYBER SECURITY | 6.5 MIN READ
Though a small business' margins are quite tight, that doesn't mean that cyber security should take a backseat. Poor cyber security can lead to ransomware attacks and other network issues that can have sizable costs to fix. .
small business cyber security,
small business cyber security solutions,
cyber security
Read More
PRINTER SECURITY | 4 MIN READ
With all the Internet-connected devices that now exist, it seems that almost any device can be targeted by a hacker. Can a printer be hacked? As a Managed Service Provider and printer dealer, our combined expertise in the.
cyber security best practices,
cyber security
Read More
CYBER SECURITY | 4.5 MIN READ
Cyber security is a complex and evolving process, which can make it difficult for businesses to efficiently and effectively protect their network from the countless cyber threats that exist. Security Operations Centers, also.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 6 MIN READ
Spyware has malicious intent, which is why individuals and businesses alike should know how it works and what threats it poses if they wish to avoid becoming a victim. So what exactly is spyware and how does it work? Keep.
cyber security
Read More
CYBER SECURITY | 5.5 MIN READ
The finance, healthcare, and legal industries are frequently targeted for cyber attacks and are also subject to multiple data privacy regulations, which makes the task of effective and compliant cyber security difficult. As.
cyber security best practices,
cyber security solutions,
small business cyber security,
cyber security
Read More
FACIAL RECOGNITION | 5 MIN READ
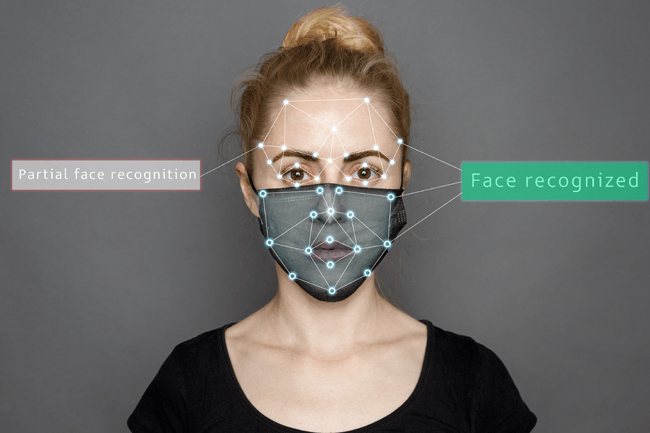
As facial recognition becomes more widely used in businesses and government entities alike, and especially due to COVID-19 causing widespread mask wearing, many are wondering if this technology can correctly identify.
cyber security solutions for small business,
cyber security,
Facial Recognition
Read More
REMOTE OFFICE | 9 MIN READ
Many companies who had their first remote trial run earlier this year amid the COVID-19 pandemic are now wondering if they should permanently keep their office remote. Keep reading to see all the factors a company should.
small business cyber security,
cyber security,
remote office
Read More
CYBER SECURITY | 5 MIN READ
While email filtering has been around in one form or another for a while, it serves a more important role in your cyber security plan than you may think. Keep reading to learn what exactly email filtering is, how it works, and.
cyber security best practices,
cyber security
Read More
MANAGED IT SERVICE | 5.5 MIN READ
Some companies may be hesitant to sign with a Managed Service Provider (MSP) when they could just hire in-house IT instead. As an MSP, we know the ways in which some MSP's taint our industry's reputation. Keep reading to.
Managed IT Services,
Managed Services Questions,
cyber security
Read More
CYBER INSURANCE | 5 MIN READ
Cyber insurance, also known as cyber liability insurance, is beneficial as a form of financial mitigation in the event of a cyber attack. However, for those unfamiliar with the industry, the jargon can make buying a policy.
cyber security,
cyber insurance
Read More
SOCIAL ENGINEERING | 5 MIN READ
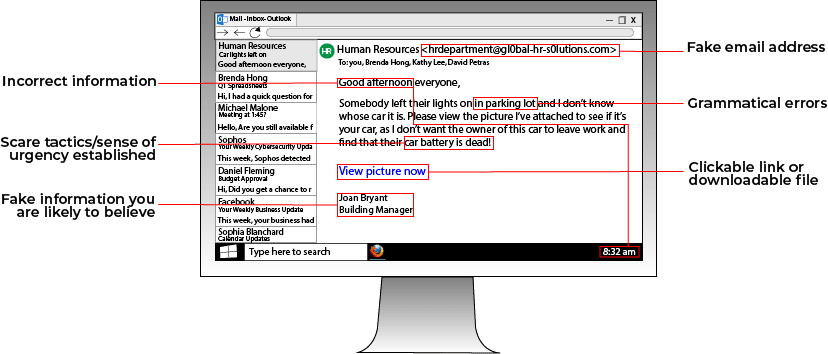
Victims of social engineering attacks can have their personal information stolen from right under their nose without ever knowing. Social engineering attacks are crafted around two basic tenants of human psychology: fear.
social engineering,
social engineering tactics,
phishing attacks,
cyber security
Read More
CYBER SECURITY | 5 MIN READ
Remote conferencing is more popular than ever before. It allows businesses the flexibility to work on their own terms without requiring clients to drive to their office. However, remote conferencing poses some potential risks.
cyber security
Read More
CYBER SECURITY | 5 MIN READ
Cyber security insurance is increasingly becoming a topic commonly discussed among business executives. As cyber threats continue to increase, more businesses begin to evaluate the need for a cyber security policy within their.
cyber security,
cyber security insurance
Read More
CYBER SECURITY | 8.5 MIN READ
Setting up a home office, especially when your office usually isn't remote, can seem daunting. However, by answering a few simple questions and pre-planning, you can save yourself a headache later. As a Managed Service.
cyber security,
remote office
Read More
CYBER SECURITY | 5 MIN READ
Cyber security laws are rapidly evolving, making some businesses quickly feel left behind. Penalties for non-compliance can be harsh, which raises the pressure for businesses to stay ahead of new legislation. How can your.
cyber security laws,
cyber security
Read More
CYBER SECURITY | 7 MIN READ
Since the rise of the Internet in the 1990's, government officials worldwide have been scrambling to keep up with the fast-paced nature of technological developments. Just twenty years ago, self-driving cars were an.
cyber security
Read More
CYBER SECURITY | 4 MIN READ
The right Managed Service Provider can be a great asset to your business. Besides keeping your network running smoothly and keeping your company's personal data out of the hands of hackers, an MSP can also take steps to.
Managed IT Services Atlanta,
Managed Services Questions,
cyber security
Read More
CYBER SECURITY | 4 MIN READ
Weak passwords are one of the easiest ways to give a hacker access to your network. Strengthening your passwords and protecting where they're stored better leverages your cyber security infrastructure. Keep reading to learn.
cyber security
Read More
MANAGED IT SERVICES | 4 MIN READ
Maximizing productivity and efficiency is a business goal that is always top-of-mind for companies. Businesses looking to achieve this may think of ways to streamline their sales process or supply chain. However, many.
Managed IT Services,
cyber security
Read More