CYBER SECURITY | 6 MIN READ
In some ways, maintaining the network security of a regular office can be easier than managing a remote office. As a Managed Service Provider, we aim to use our cyber security expertise to educate our audience about how to.
cyber security
Read More
CYBER SECURITY | 9 MIN READ
Varying the passwords you use for everything from your email account to your company's HR database is a great first step at protecting your data, but what happens when you have so many passwords that you begin to lose track of.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
MANAGED IT SERVICES | 5 MIN READ
If you're reading this article, then deep down you probably already know that it's time to cut ties with your MSP. If you're still on the fence, you might want to know what factors to keep in mind when making the decision.
Managed Services Questions,
cyber security
Read More
CYBER SECURITY | 13 MIN READ
If your company is looking to transition your office to work remotely, you might be wondering how to make that transition, especially when your office currently has little to no remote workers. From a technical perspective,.
cyber security
Read More
DARK WEB | 4 MIN READ
A place rumored to be full of illicit activity, the dark web's mystery intrigues many.Because the dark web is an in-tangible concept hidden away in the corners of the Internet, i t can be hardfor one to even grasp what the dark.
dark web,
cyber security
Read More
CYBER SECURITY | 7 MIN READ
The healthcare industry must follow strict protocol to remain compliant with HIPAA. Because many organizations within the industry store private information like patient files and financial information, the industry as a whole.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 7 MIN READ
If you're currently in the market for a managed services provider, you might have seen or will come across a contract spelling out your services agreement. Managed IT services contracts can come with terms that might confuse.
Managed IT Services,
cybersecurity,
Managed Services Questions,
cyber security
Read More
CYBER SECURITY | 8 MIN READ
The legal industry ranks among the healthcare and finance sectors as one of the most targeted industries for cyber attacks. The common thread that makes them attractive targets is the personal information that they store and.
small business cyber security,
small business cyber security solutions,
cyber security
Read More
CYBER SECURITY | 7.5 MIN READ
As a Managed Service Provider, our clients ask us about the benefits of cloud versus on-premise security all the time. Data security is becoming more and more crucial for businesses as cyber attacks are on the rise, which.
cyber security solutions for small business,
small business cyber security,
small business cyber security solutions,
cyber security
Read More
DARK WEB | 6 MIN READ
While the future of the dark web, a magnet for criminal activity, is un-predictable in many ways, there are growing trends in both its audience and functionality. Read more to discover what dark web trends we predict will continue.
dark web,
cybercrime,
cyber security
Read More
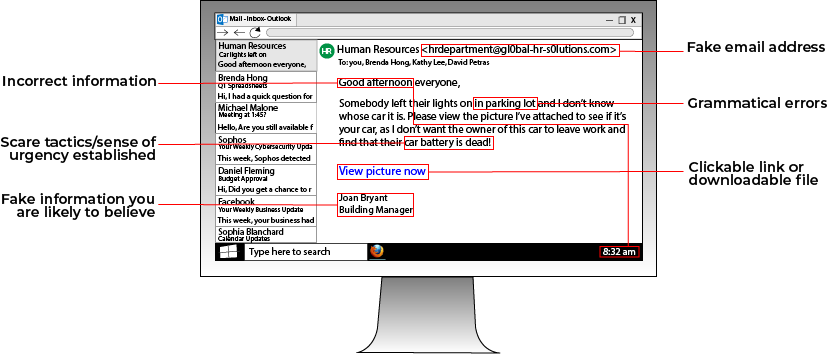
SOCIAL ENGINEERING | 4.5 MIN READ
Social engineering threatens your business' livelihood. By preying on human emotion to access sensitive information and hack your network, social engineering can cause a host of negative consequences. Read more to find.
social engineering,
social engineering techniques,
social engineering scenarios,
cyber security
Read More
CYBER SECURITY | 5 MIN READ
As a managed IT services provider, we strive to use our industry knowledge to clear up any frequently asked questions for our audience. A network security key, also known as your Wi-Fi password, is a phrase that can confuse.
cyber security
Read More
SOCIAL ENGINEERING | 5 MIN READ
Whaling is a common term used to describe the hunting of whales for the oil that their blubber produces. In Las Vegas, the term "whale" is used to describe gamblers who are prepared to bet large sums of money at the.
whaling social engineering,
cyber security
Read More