
CYBER SECURITY | 6 MIN READ
Your home's Wi-Fi network may not be as secure as you think. As a Managed Service Provider, we assist offices in remote transitions, which involves securing these employees' work devices and data that are connected to their Wi-Fi network. Keep reading to use our expertise and be guided through how to secure your home's WiFi network.
Not enough time? Jump to:
Top 7 Home Wi-Fi Security Tips
Cyber Security Tips for Remote Workers
Top 7 Home Wi-Fi Security Tips
Utilize a Strong Password
Many routers come with a default password. While this default password seems hard to crack, manufacturers tend to use the same types of passwords. Hackers knowingly exploit this weakness to hack your home's network.
We recommend changing your default password to a stronger alternative using the following tips:
-
Use a Variety of Characters− Construct your password with a variety of uppercase and lowercase letters as well as numbers and symbols. Be sure to not use common character substitutions such as 1 for l and @ for a, as hackers know and exploit these when attempting to crack passwords.
-
Use a Long but Purposeful Password− In general, the longer a password is, the longer it will take a hacker or computer to crack it. However, don't just add characters for the sake of making your password longer, as this can lead to insecure practices such as popular character substitutions and repeated phrases (ex. fourfourfour) that can make a password easy to crack.
-
Don't Include Easy-to-Find Personal Information− Personal information such as birthdays and pets' names are easy to find if one peruses your social media accounts. Refrain from including this kind of information in your passwords.
Enable a Guest Network
If your router has a guest network that can be enabled, we recommend that you do so. Guest networks let visitors access your Wi-Fi network without accessing the rest of your network or being able to change Wi-Fi settings.
Additionally, if possible, hide the name of your Wi-Fi network, as this makes it harder for hackers to locate and access your network.
Update Your Router’s Software
Similar to your antivirus, your Wi-Fi router also needs to be updated to ensure that security flaws are patched and your router is kept up-to-date.
If you don't periodically update your router when updates become available, newly discovered security flaws won't be fixed, which leaves your router open to hackers.
Use a Good Firewall

Firewalls protect your network and its devices from hackers by closely monitoring traffic coming in and out of your network and blocking anything deemed a threat.
Some modern routers come with built-in firewall capabilities. However, if you're a remote worker whose work device contains a significant amount of sensitive data, you should consider asking your office to give you your own firewall to install in addition to your router.
Hybrid router-firewalls aren't that secure, so company data would be better protected from both a router and a firewall.
Use VPN's
Virtual Private Networks, also known as VPN's, can be used in conjunction with an existing Wi-Fi network to ensure that data is encrypted when it's sent to and from your office. VPN's also anonymize an employee's web traffic when they're working remote and using a less secure Wi-Fi signal, for instance at Starbucks or in their house.
VPN's authenticate your information with your network's firewall before allowing it through, which ensures that information is encrypted and your network is secure when all employees are sending information, logging into programs, and communicating with each other.
If you're a remote worker that needs to better secure your data, consider buying and installing a VPN.
RELATED: What is a VPN?
Enable Network Encryption Features
Many routers come with encryption features, which can help secure data stored and shared on your network. If these features are turned off, consider turning them on.
One of these features can be the type of network security key, also known as a Wi-Fi password, that you enable. The most common types of network security keys are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA/WPA2) .
WPA and WPA2 are more secure network security keys than WEP. A WPA comes with a password/passphrase that you can obtain from the network's owner. The password that you sometimes see printed on the side of your router is the WPA key.
Usually with these kind of networks, the owner can reset the WPA key to be whatever password or passphrase they want.
WPA2 is an even more secure version of WPA because it uses the AES algorithm, a newer, faster, and more advanced algorithm than what was previously used.
WPA2 is usually the recommended version for businesses with remote workers. Keep in mind, however, that to use WPA2, you might need hardware with a higher processing power.
Disable Insecure Router Features
Routers come with a variety of features designed to improve the user experience. However, some of these features come with security flaws. We recommend that you turn the following features off if your router has them:
Remote Access
Remote access features make it easier to access your router's settings on the go. However, hackers can exploit this feature to gain access to your network. Most people will likely never need to access their router remotely, so it shouldn't affect you that much to turn this feature off if your router has it.
Universal Plug-and-Play
This feature makes it easier for devices such as gaming consoles and smart TV's to access the Internet. However, it can also be used by malware programs to access your router's security settings.
Wi-Fi Protected Setup
Wi-Fi Protected Setup simplifies the connection process for devices on your network so that all it takes is a push of a button or a PIN code. However, numerical PIN's are much easier to crack than a standard password. Consider turning this feature off if your router has it.
Cyber Security Tips for Remote Workers
Secure Your Printers
Personal copiers and printers, especially older models, used in managers' offices come with a host of security risks. Since these machines are usually intended for home use, security isn't as much of a priority when brands build them.
For instance, "home copiers" can have a "print from anywhere" feature that lets you print documents to the copier even when you're away from the office. However, this "print from anywhere" feature has little security because it has to create a hole in your firewall to allow you to communicate with the machine from anywhere in the world.
This hole in your firewall can let a hacker access the machine and anything scanned on it, documents and files on that employee's computer, and even access the whole company's network. If you have this feature on your personal printers, turn it off.
Another security gap on personal machines that you might not consider is a default setting that, when you're scanning to the hard drive on a copier, allows you to open the folder from computers on the network to retrieve your files.
This setting allows for information to be written to and removed from that device from anywhere on your company's network and is generally done with minimal or no security. If your personal copiers and printers have this default setting, turn it off.
RELATED: How Can Your Printers Have Security Risks? [Tips to Protect]
Implement Secure File-Sharing
Secure file-sharing platforms ensure that business continues to flow smoothly and securely.
Platforms such as OneDrive or ShareSync let you open and view your synced files directly from your phone and safely share them with co-workers and clients.
Business phones may also come with a feature called “Find Me Follow Me”, or twinning. With this feature, calls are forwarded from an employee's desk phone to their mobile phone.
If that employee doesn’t pick up after a few rings, instead of letting someone leave a voicemail on their mobile phone, which can mean that sensitive information is now stored on an employee's personal device, the call is re-routed back to that employee's desk phone so someone can leave a voicemail there instead.
Then, a transcript of the voicemail is emailed to that employee. This feature lets you control where your company's data is stored by ensuring that no voicemails that may contain sensitive data are left on an employee's personal device.
Detect and Avoid Phishing Attacks
Hackers know that remote workers mainly rely on email for communication, which is why they frequently use email phishing attacks to exploit and hack your network.
Phishing attacks involve a hacker sending an email containing a malware-loaded link to a potential victim.
The email can either contain an enticing offer, such as "Click this link for a free cruise!' or can be faked to resemble a legitimate company. For instance, a hacker posing as Google could email a victim telling them to click a link to update their email storage.
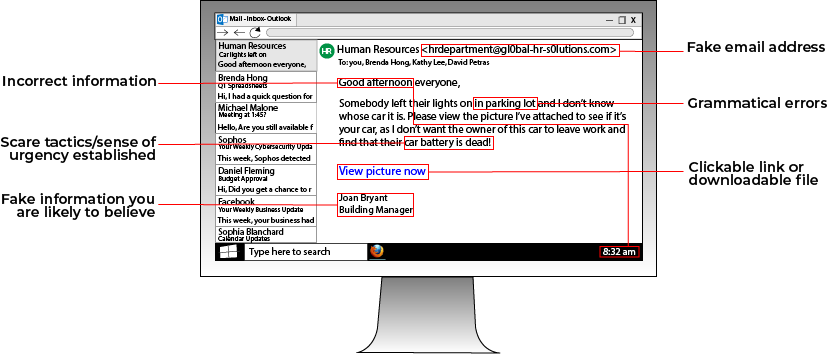
As the graphic above shows, there are various red flags to look for in emails to see if it's a potential phishing attack. For instance, you should always be wary of
As the graphic above shows, there are various red flags to look for in emails to see if it's a potential phishing attack. For instance, you should always be wary of emails from people you don't know telling you to click a link.
If you want to see if an email is a phishing email, you can look at the address that the email is from. For instance, a phishing email posing as Facebook that has the email address "security@fakebookalerts.live" is probably a fake address.
Make sure that the address is spelled correctly too with no character substitutions. While an address from "@facebook.com" might be legitimate, an email from "@facebo0k.com" is probably a phishing attempt.
Another way to test a phishing email is to try and find the page the email is referencing without clicking the link. For instance, if the email is from Microsoft and is telling you to update your storage, try doing that through the official Microsoft website instead of through the link. If you can't find such a page, then the email is most likely a phishing attempt.
RELATED: 5 Cyber Security Tips for Remote Workers
Home Wi-Fi is such an integral part of daily life that many of us overlook the ways our data' security could be at risk because of it.
We hope that you can use this blog to better secure your home's Wi-Fi and protect your sensitive data.
For more cyber security content, follow our blog!
Posted by Andre Schafer

Andre Schafer is a Technical Account Manager at Standard Office Systems. He has spent his entire career in the Office Technology and IT fields. For nearly 30 years, he has held various roles, including Technician, Trainer, Analyst, and Account Manager. Andre’s focus has always been to understand his customers' business needs to provide the appropriate technologies and services.


