
CYBER SECURITY | 5.5 MIN READ
In our rapidly changing world, it's hard to predict what somebody might have for breakfast tomorrow, let alone how ransomware will change in the coming years. Read more to learn about developing ransomware trends that could shape the world as we know it for years to come.
Not enough time? Jump to:
Rise in Attacks on Government Agencies
Increased Attacks on Large Corporations
Increased Use of RaaS

Ransomware as a Service, also known as RaaS, has been gaining popularity over the past few years. RaaS is when a hacker creates a ransomware code and then sells it to inexperienced hackers.
These hackers can then use the code to carry out their own ransomware attacks as long as they give some of the profit to the ransomware's creator.
Cerber is one of the most prominent examples of the Ransomware-as-a-Service model. Because it was distributed to hackers worldwide, Cerber attacks were widespread in 2016. According to Helpnet Security, as of August 2016, “Cerber had been running 161 active campaigns, targeting 150,000 users in 201 countries in July alone”.
Since RaaS is both profitable and gives inexperienced hackers opportunities to deploy ransomware attacks, we predict that these types of attacks will increase in the coming years.
RELATED: How Ransomware Has Evolved
More File Publishing

When the threat of permanently deleting sensitive files doesn't coerce victims into paying a ransom, cyber criminals have recently turned to another form of intimidation − threatening to publish stolen files online if the ransom isn't paid.
For instance, in October of 2015, a strain of ransomware known as Chimera gained publicity when its creators said that they would publish a victim’s stolen files online if they didn’t pay the ransom.
Just last month, the Sodinokibi/REvil ransomware, which also threatens to publish data if the ransom isn't paid, was used to attack Travelex, the world's biggest currency exchange company.
While permanently losing access to your files is a sticky enough situation to be in, having your personal files published online means that businesses can face a host of other potential consequences.
If your business is in the healthcare industry, files that are stolen and published online could potentially put you in breach of HIPAA. Additionally, businesses whose customer information is published online could face lawsuits.
Though the idea of being sued for files taken and published without your permission sounds far-fetched, the government, in an effort to protect citizens' private data, is passing laws cracking down on data breaches. The government hopes that these laws will motivate businesses to strengthen their cyber security measures.
No matter the consequences of a ransomware attack, Sodinokibi and Chimera showcase how this type of attack is both successful and here to stay.
Rise in Attacks on Government Agencies

According to CNN, in 2019 over 140 local governments, police stations and hospitals were victims of ransomware attacks. This trend shows no signs of slowing down.
Hackers don't discriminate when it comes to the types of businesses and systems they target. Government agencies, which many assume to have some of the most secure networks in the country, can and do fall victim to data breaches and cyber attacks.
Government agencies protect sensitive information but don't always have the budgeted resources for adequate cyber security. This makes them easier targets for ransomware and potentially more likely to pay a ransom out of a desperation to get their files back.
Forbes just recently reported on how cyber attacks on government agencies are actually becoming more and more common. This is because government agencies' interactions with third-party companies as well as their network configuration makes the possibility of a widespread attack easier.
For instance, Electronic Warfare Associates, a government contractor with clients like the Department of Defense, the Department of Justice, and the Department of Homeland Security fell victim to a ransomware attack last month.
Even our voting systems are open to hacking, as seen by an 11-year-old who, at a hackathon in 2018, breached a replica of a Florida online voting system and changed the results of the fake election in just ten minutes.
If these systems can be hacked, what does that say about how safe the rest of our networks are? Though the trends of ransomware attacks on government agencies is alarming, it shows an increased need for companies to strengthen their cyber security measures.
Increased Attacks on Large Corporations

Though large corporations typically have the budgets to implement extensive cyber security measures, a sophisticated hacker or group of hackers motivated by the potential for a large profit can find their way into a network.
An easy way for hackers to break into even the most secure network is through phishing emails. If a hacker sends a legitimate-looking email containing a link to ransomware to employees at a company and just one employee is tricked into clicking the link, then sometimes even the most robust and secure network can become compromised.
Hackers know that, unlike computers, humans are prone to errors, which is why they can be exploited to gain access to and infect a network no matter how secure it is.
The Ryuk ransomware attacks of 2018 showcase just how lucrative large-scale attacks can be. Aimed more so at large corporations, Ryuk's “big game hunting” has earned those who deploy it an estimated collective profit of $3 billion.
This amount is only increasing, seeing as Ryuk attacks have been carried out up through last year. Ryuk's profitability shows the potential earning power of targeting a large corporation.
How to Prevent Ransomware
Know How to Spot a Phishing Attack
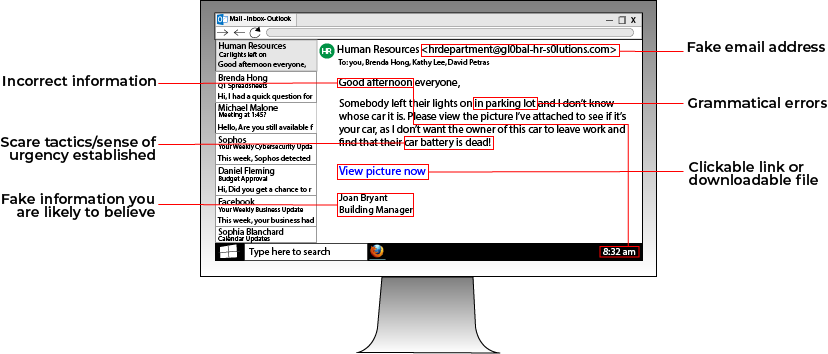
A popular way that hackers deploy ransomware and gain access to a network is through phishing attacks. Phishing attacks involve a hacker sending an email containing a malware-loaded link to a potential victim.
The email can either contain an enticing offer, such as "Click this link for a free cruise!' or can be faked to resemble a legitimate company. For instance, a hacker posing as Google could email a victim telling them to click a link to update their email storage.
Always be wary of emails from people you don't know telling you to click a link. If you want to see if an email is a phishing email, you can look at the address that the email is from. For instance, a phishing email posing as Facebook that has the email address "security@fakebookalerts.live" is probably a fake address.
Make sure that the address is spelled correctly too with no character substitutions. While an address from "@facebook.com" might be legitimate, an email from "@facebo0k.com" is probably a phishing attempt.
Another way to test the legitimacy of a phishing email is to try and find the page the email is referencing without clicking the link. For instance, if an email from Microsoft is telling you to update your storage, try doing that through the official Microsoft website instead of through the email's link. If you can't find such a page, then the email is most likely a phishing attempt.
In general, most legitimate emails don't ask you to click a link to validate or update information, so your internal warning signals should flash as soon as you see this. If you feel suspicious about an email, try calling the company who it's from to ask about the email, along with other verification methods.
RELATED: What is Phishing? [Types and Tips to Prevent]
Strengthen and Protect Your Passwords
Weak passwords are one of the easiest ways that a hacker can break into your network and install ransomware. Consider strengthening your passwords and protecting where they're stored to better leverage your cyber security infrastructure.
A main focus of any password policy should be to limit how much you write down your passwords, whether they're on a sticky note, an Excel spreadsheet, or in the Notes app on your phone. Writing a password down anywhere leaves it susceptible to being found by hackers.
If you write account passwords down on your phone, all it takes is your phone being stolen or your iCloud account being hacked for somebody to have the logins to accounts that contain sensitive information such as your credit card number.
If you have too many passwords to remember, consider a secure password-storing program such as MyGlue.
To maintain strong passwords, consider changing passwords every six months and creating passwords that don't use easy-to-find information such as birthdays or your children's names. When creating a password, make sure it's long and complex.
Additionally, install two-factor authentication on your devices if possible, seeing as it's a widely used secure method of protecting accounts.
RELATED: Cyber Security Awareness Training for Employees [Tips]
Consider Managed IT Services

If you are a business, you might not have the time to institute all these changes, especially if you only have an in-house IT manager or another employee managing your cyber security.
Managed IT services can help put all of the above suggestions and more into action. Managed IT services layers your cyber security infrastructure and then employs a team of IT experts to address any threats or issues that pop up.
A managed services provider can use dark web scans and network scanning tools to address existing security gaps. Then, they can install layers of cyber security hardware and software, such as firewalls, anti-virus software, and anti-ransomware software.
They can conduct phishing tests to find employees who fall for phishing traps, and then educate those employees on how to recognize and avoid phishing attacks. To take phishing prevention a step further, a managed services provider can enable email filtering services to stop phishing emails in their tracks.
Managed IT services can help you create a password policy that works for your business too. Additionally, in the event that a ransomware attack happens or your network goes down, they can reduce downtime by quickly recovering data due to their use of frequent and secure backups.
Don't wait until you're the victim of a ransomware attack to improve your cyber security.
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

