Erica Kastner
Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.
CYBER SECURITY | 4.5 MIN READ
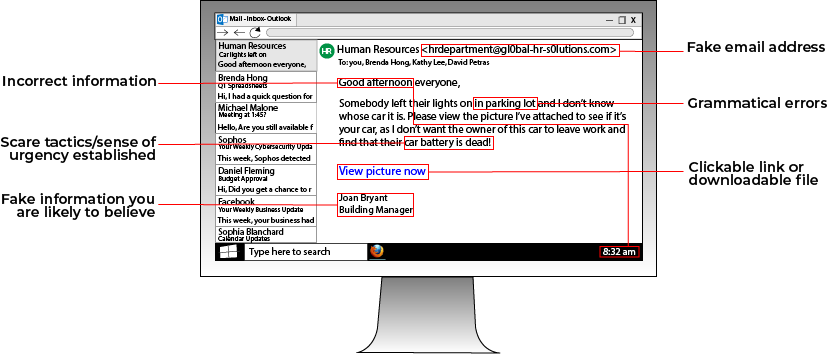
When you transition from a corporate office to a home office, the task of keeping your remote environment secure from cyber threats and malicious actors can seem complex. As a Managed Service Provider, we assist clients in.
cyber security solutions,
small business cyber security,
remote office
Read More
DATA BACKUP | 5 MIN READ
Many businesses know that data backups are an integral aspect of data security. However, the tasks of determining how often to back up data and the best backup protocol can be complex. As a Managed Service Provider, we assist.
cyber security,
BCDR plan,
Data Backup
Read More
CYBER SECURITY | 6.5 MIN READ
Though a small business' margins are quite tight, that doesn't mean that cyber security should take a backseat. Poor cyber security can lead to ransomware attacks and other network issues that can have sizable costs to fix. .
small business cyber security,
small business cyber security solutions,
cyber security
Read More
RANSOMWARE | 4.5 MIN READ
Ransomware attacks are on the rise as more cyber criminals see the lucrative advantages of targeting businesses' networks. As a Managed Service Provider, we aim to use our ransomware expertise to educate the public on emerging.
what is ransomware,
ransomware and phishing
Read More
CYBER SECURITY | 5 MIN READ
Businesses looking for assistance managing employee network help requests may turn to a Network Operations Center. However, what are the unique benefits that of a NOC that differentiates it from a help desk? Keep reading to.
Managed IT Services,
Network Security,
cybersecurity
Read More
REMOTE WORK | 5.5 MIN READ
Your remote employees may be unknowingly putting your company's data at risk. Working from home can potentially lead to data breaches, identity fraud, and a host of other negative consequences. Keep reading to learn the top.
cybersecurity,
remote office
Read More
CYBER SECURITY | 7.5 MIN READ
Effective corporate cyber security has never been more important. Security advice is dynamic, which means that your business' network needs to evolve to stay ahead of emerging cyber threats. Keep reading to learn our top.
Read More
MANAGED IT SERVICES | 6 MIN READ
Companies looking for cyber security assistance may not know what a NOC is, especially when compared to a help desk, when they come across it in a Managed Service Provider's offering. As an MSP with an in-house NOC, we.
Read More
MANAGED IT SERVICES | 5.5 MIN READ
As a Managed Service Provider, we understand that not every business will be the right fit for us. For instance, some businesses may be a better fit for an internal IT department. Keep reading to learn who is a good.
Managed IT Services
Read More
MANAGED IT SERVICES | 7 MIN READ
As a Managed Service Provider, we aim to take customer service a step further by not only educating our clients about how to secure their data but also by educating the public. Although securing company data is a top.
Managed IT Services
Read More
CYBER SECURITY | 4 MIN READ
IT professionals and cyber criminals are constantly performing a sort of dance together. When cyber criminals move one way, IT professionals must move in response, and vice versa in a never-ending salsa. Since cyber criminals'.
cybersecurity
Read More
CYBER SECURITY | 6 MIN READ
Acts of Mother Nature and the wrath of cyber criminals can be unpredictable. If your business' network went down tomorrow due to a natural disaster or cyber attack, how would you ensure that business operations continue.
cybersecurity,
BCDR plan
Read More
PHISHING | 4.5 MIN READ
Criminals will take advantage of any new and unfamiliar situation to steal people's personal information and scam them out of money. The COVID-19 pandemic has provided criminals with a wealth of new opportunities to steal from.
what is phishing,
phishing attacks
Read More
PRINTERS | 4 MIN READ
When you're shopping for a new printer, whether it's for your office or your house, you will typically come across two types of printers: laser and inkjet. As a metro-Atlanta based copier/printer dealer, we aim to use our industry.
advantages and disadvantages of laser printers
Read More
CYBER SECURITY | 5 MIN READ
When natural disasters and cyber attacks strike, the consequences can extend far beyond just physical damage. Your network functionality may be crippled and severe downtime can cost your business more money than you think..
Read More
CYBER SECURITY | 5 MIN READ
Business Continuity and Disaster Recovery (BCDR) plans help organizations mitigate the risks associated with network downtime and interruptions to business operations. Keep reading to learn what a BCDR plan is, how your.
cybersecurity,
small business cyber security
Read More
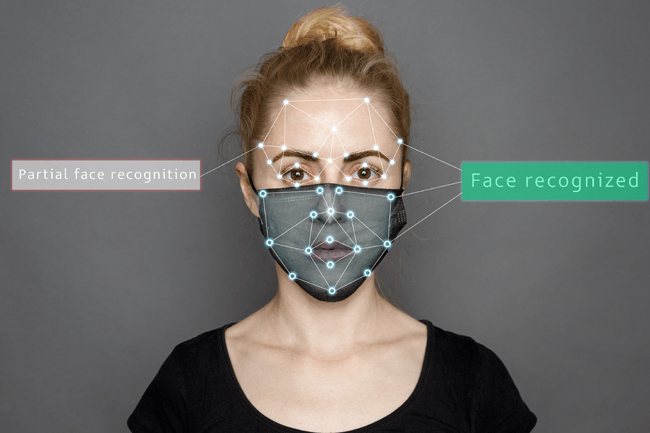
FACIAL RECOGNITION | 5 MIN READ
As facial recognition becomes more widely used in businesses and government entities alike, and especially due to COVID-19 causing widespread mask wearing, many are wondering if this technology can correctly identify.
cyber security solutions for small business,
cyber security,
Facial Recognition
Read More
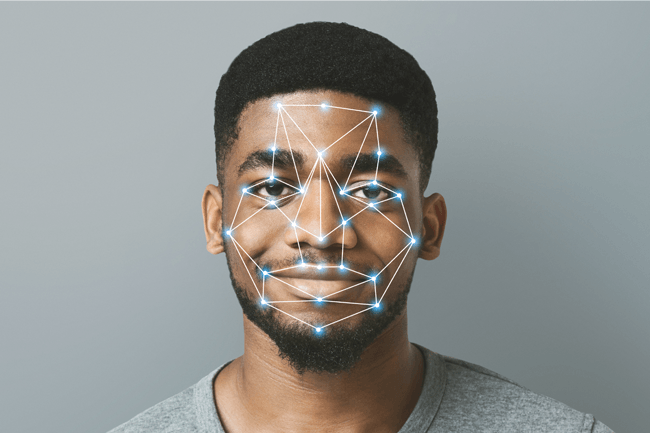
FACIAL RECOGNITION | 6 MIN READ
Facial recognition is a buzzword that's been the topic of many news articles and the subject of various movies. While some see this technology as dystopian, others see it as a futuristic way to further streamline our.
Read More
CYBER INSURANCE | 4.5 MIN READ
Thoughcyber insurance can provide significant financial coverage in the event of a cyber attack or data breach, policy costs can quickly add up. Luckily, there's a few steps your organization can take to keep costs low. .
Read More
TEMPERATURE SCANNERS | 5.5 MIN READ
As COVID-19 continues to impact business operations, many companies are wondering how to minimize its spread and safely keep their doors open. Infrared temperature scanners offer businesses a solution that, when used.
Temperature Scanners
Read More