
CYBER SECURITY | 5 MIN READ
As a managed IT services provider, we strive to use our industry knowledge to clear up any frequently asked questions for our audience. A network security key, also known as your Wi-Fi password, is a phrase that can confuse those outside of technical industries. Understanding jargon like this is the first step in learning how to better secure your network. Read more to learn what a network security key is, what types exist, where you can find it, and tips on how to better protect your network.
Not enough time? Jump to:
What is a Network Security Key?
What Are the Different Types of Network Security Keys?
Where Can I Find My Network Security Key?
How Can I Better Protect My Network?
What is a Network Security Key?
In simple terms, a network security key is another name for your Wi-Fi password.
A network security key is a kind of network password/digital signature that one enters as authorization to gain access to a wireless network.
Network security keys also establish secure connections between the user requesting access and the network or wireless device. This protects a network and its associated devices from unwanted access.
When you have a weak network security key, you leave your network open to access by cyber criminals. If a cyber criminal is able to access your personal information, it can be sold on the dark web or can lead to identity theft and other serious consequences.
RELATED: How Hackers Get Your Business' Personal Information
What Are the Different Types Of Network Security Keys?

The most common types of network security keys are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA/WPA2) .
WEP
A WEP key is a security passcode for Wi-Fi-enabled devices. WEP keys let devices on a network exchange encrypted messages with each other while blocking those messages from being easily decoded and read by outsiders.
WEP keys are a sequence of characters taken from the numbers 0 through 9 and the letters A through F. For instance, a WEP key could be F45HI00WR3.
The required length of a WEP key could be 10, 26, or 58 characters long, depending on which WEP version is running. WEP keys can be automatically generated for ease of use. When they're not, there are websites that generate random hard-to-guess WEP keys for you.
WEP keys lost public favor when people began to realize that they are easy to crack, which leaves your network potentially open to hackers.
WPA/WPA2
WPA and WPA2 are more secure network security keys than WEP. A WPA comes with a password/passphrase that you can obtain from the network's owner. If you have a Wi-Fi router at home, the password that you sometimes see printed on the side of it is the WPA key.
Usually with these kind of networks, the owner can reset the WPA key to be whatever password or passphrase they want.
WPA2 is an even more secure version of WPA because it uses the AES algorithm, a newer, faster, and more advanced algorithm than what was previously used.
WPA2 is usually the recommended version for businesses, who tend to need heightened security measures. Keep in mind, however, that to use WPA2, you might need hardware with a higher processing power.
RELATED: 15 Cyber Security Statistics You Need to Know
Where Can I Find My Network Security Key?
Has your computer been asking you to enter your network security key? If so, you may not know where to find it.
Usually, your router has a sticker that lists the Wireless Network Name, also known as a SSID, and the Wireless Security Key Password, which is your network security key. Network security keys are a combination of characters, for instance F23Gh6d40I.
If your computer is already connected to your Wi-Fi and you cannot remember the security key and need to find it, you can also find it by going to the settings on your computer. Keep in mind that the following steps will only show you your password if your device is already connected to your Wi-Fi network.
Finding the Network Security Key on Windows
If you have Windows 10, follow the steps below to find the key in your settings.
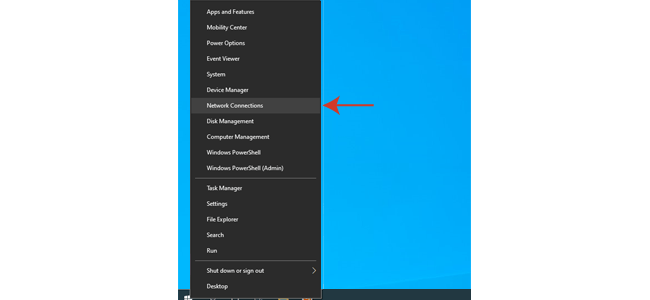
2. Click on "Network and Sharing Center".
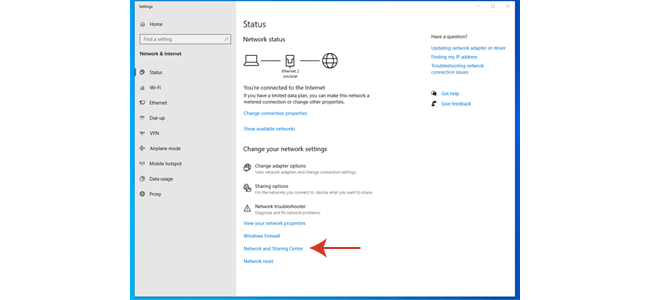
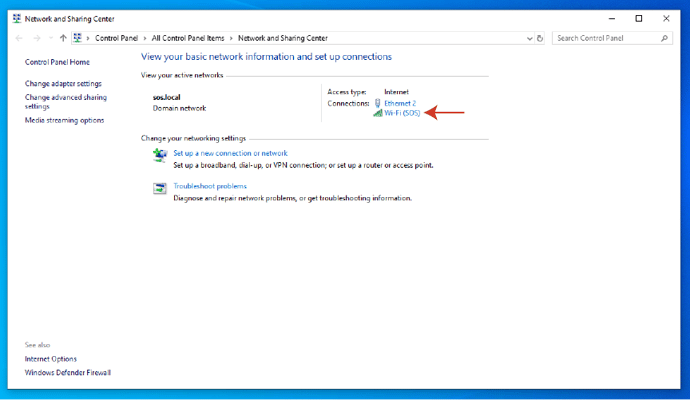
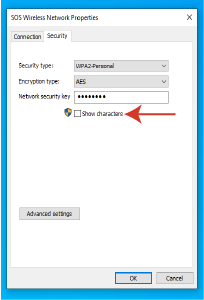
4. Click on the "Wireless Properties" button and then on the Security tab.
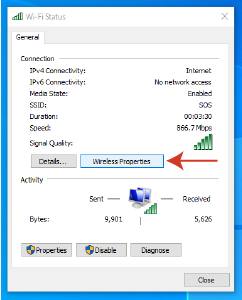
5. Select the "Show Characters" checkbox to reveal your network security key.
Finding the Network Security Key On a Mac
If you have a Mac, you can find your network security key by following a few simple steps.
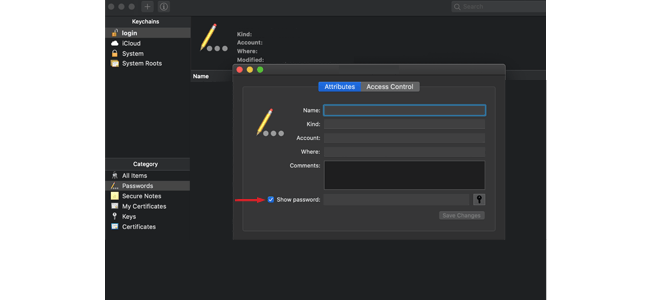
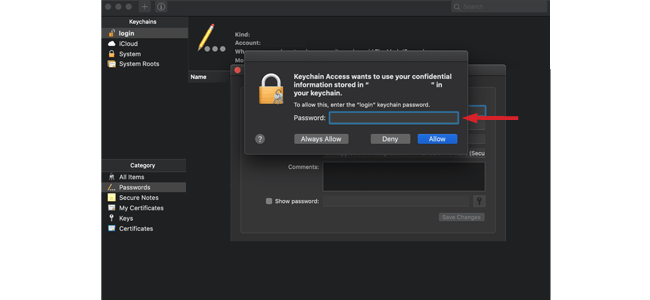
RELATED: How Can Your Printers Have Security Risks? [Tips to Protect]
How Can I Better Protect my Network?

Create a Strong Network Security Key
Weak passwords are one of the easiest ways to give a hacker access to your network. If you have a WPA/WPA2 key that you can select yourself, consider strengthening it and protecting where it is written down to better leverage your cyber security infrastructure.
In general, you should limit how much you write down your passwords, whether they're on a sticky note, an Excel spreadsheet, or in the Notes app on your phone. This piece of advice extends to writing down your Wi-Fi passwords anywhere too.
Writing a password down anywhere leaves it susceptible to being found by hackers. If a hacker were to gain access to your network, there is no telling the havoc that they could wreak.
Consider changing your network security key and other passwords every six months to keep them fresh and secure. Additionally, when creating a password or security key, don't use easy-to-find information such as birthdays or your children's names.
When creating a password, make sure it's long and complex. To make your passwords more complex, try creating a "passphrase" instead. Passphrases involve picking a meaningful phrase that you can remember, and making the first letter of every word the password.
RELATED: How Can I Create and Secure a Strong Password?
Keep Firewalls, Routers, and Antivirus Software Up-to-Date
Firewalls keep would-be intruders where they should be– outside your network. By putting up a virtual “wall” against inbound and outbound traffic, firewalls choose whether to allow or block certain traffic through.
Antivirus software is great at scanning incoming files and code for known viruses and malware. Installing antivirus on your computer should be one of the first tasks you complete when you get a new computer, as it will help protect against Internet threats.
Firewalls and antivirus software serve as a good basis for building your network security. While installing firewalls and antivirus software are both great methods for securing your network, many people forget or push off updating them.
While we know this process can be a nuisance, every day that you wait to update your firewall and antivirus after new versions emerge leaves you more vulnerable to cyber attacks.
Software updates are used to patch newly discovered security gaps. When you push off updating your security software, you leave yourself open to a cyber criminals exploiting these security gaps to hack into your accounts and steal your personal data.
If you are able to, enable auto-updates on your security software and schedule any updates for late at night when you're not using your computer. This will ensure that even if you forget to manually complete an update, it will still happen regardless.
RELATED: How Does Antivirus Work?
Consider Managed IT Services
If you are a business, you might feel overwhelmed with managing your cyber security infrastructure. Managed IT services can, among many other tasks, help you create a company-wide password policy that works for your business.
Additionally, managed IT services proactively handles your network's security by implementing safety measures, and then employ a team of IT experts to address any threats or issues that pop up.
In the event that a ransomware attack happens or your network goes down, they can reduce downtime by quickly recovering data due to their use of frequent and secure backups.
RELATED: What are Managed IT Services?
We hope that this article answered your questions and taught you a few tips about network protection. For more cyber security-related content, follow our blog!
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

