
CYBER SECURITY | 5 MIN READ
Business Continuity and Disaster Recovery (BCDR) plans help organizations mitigate the risks associated with network downtime and interruptions to business operations. Keep reading to learn what a BCDR plan is, how your organization can build one, and how else you can protect your data.
Not enough time? Jump to:
How Else Can I Protect My Data?
What is a BCDR Plan?
BCDR plans are utilized by businesses in the event of network outages stemming from natural disasters or cyber attacks to:
-
Ensure that operations run smoothly
-
Minimize network downtime
-
Minimize data loss
Business Continuity plans re-direct resources, establish chains of command, and coordinate shifts in employees so that business operations have minimal interruptions during natural disasters and network outages.
For instance, if a tornado swept through and destroyed part of a business' office, how would the company continue to ensure that all employees have web access and know how to continue working?
In this scenario, maybe all employees would be instructed to work remotely, or maybe some business functions would temporarily be put on pause to direct resources to more critical business tasks.
Disaster Recovery plans mainly focus on how to utilize effective IT to quickly recover one's network with minimal downtime and data loss. A few main tenants of Disaster Recovery plans include server and network restoration and backup recovery.
RELATED: BCDR Plans [Why All Businesses Should Have Them]
How Do I Build a BCDR Plan?

If your company doesn't have a BCDR (Business Continuity Disaster Recovery) plan, you are at a disadvantage for when a natural disaster or cyber attack happens. Building out and regularly testing a thorough BCDR plan puts you a step ahead for when disaster strikes.
When building a Business Continuity plan, evaluate the workflow for all departments. Since many jobs can now be done online, in the event that your network goes down, many employees should still be able to work remotely from home and use websites and other online platforms to continue working.
When evaluating each department, answer some of the following questions: How do they communicate with one another? What software and programs do they use? How much of their jobs rely on files within your network? Knowing the answers to questions like these can ensure that there are no gaps in your plan.
When your network goes down, key files may not be easily accessible company-wide. This can hinder productivity, which is why an effective Disaster Recovery plan can make all the difference in the world.
A crucial part of any Disaster Recovery plan is automating backups. Network outages and ransomware attacks can happen at any time. In these scenarios, you may have to restore all devices to the most recent backup. If you don't back up data frequently, then you risk losing access to important documents. Automating backups minimizes data loss and downtime.
Additionally, when creating a Disaster Recovery plan, make sure that all executives and any in-house IT staff know the proper steps to take in the event of a cyber attack or network outage.
Will all employees be shifted to remote work temporarily? Do any software vendors need to be contacted? Which employees will be the primary people to handle a network outage, and which tasks will they need to delegate to others? Answering these questions ensures that staff resources are quickly and efficiently allocated to get your network running again.
How Else Can I Protect My Data?
Know How to Spot a Phishing Attack
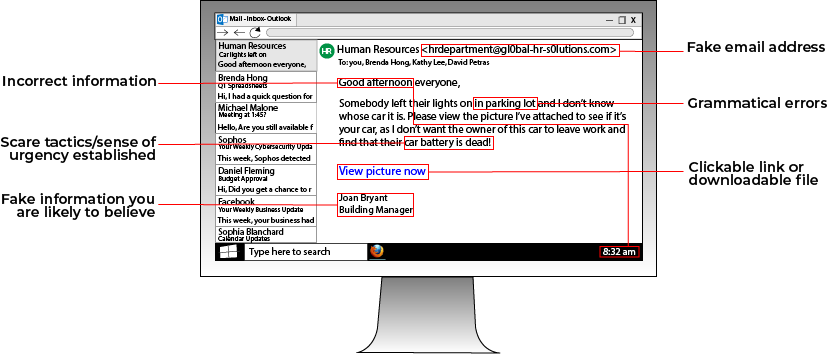
Since workers in a remote office cannot meet face-to-face, email becomes the king of communication. Hackers know this, which is why they can use phishing attacks to hack your network.
While computers are designed to not make mistakes, hackers know that humans are prone to errors. That is why they exploit human error to gain access to a network and deploy ransomware. A popular way that hackers gain access to a network is through phishing attacks.
Phishing attacks involve a hacker sending an email containing a malware-loaded link to a potential victim. The email can either contain an enticing offer, such as "Click this link for a free cruise!' or can be faked to resemble a legitimate company. For instance, a hacker posing as Google could email a victim telling them to click a link to update their email storage.
Always be wary of emails from people you don't know telling you to click a link. If you want to see if an email is a phishing email, you can look at the address that the email is from. For instance, a phishing email posing as Facebook that has the email address "security@fakebookalerts.live" is probably a fake address.
Make sure that the address is spelled correctly too with no character substitutions. While an address from "@facebook.com" might be legitimate, an email from "@facebo0k.com" is probably a phishing attempt.
Another way to test a phishing email is to try and find the page the email is referencing without clicking the link. For instance, if the email is from Microsoft and is telling you to update your storage, try doing that through the official Microsoft website instead of through the link. If you can't find such a page, then the email is most likely a phishing attempt.
In general, most legitimate emails don't ask you to click a link to validate or update information, so your internal warning signals should flash as soon as you see this. If you feel suspicious about an email, try calling the company who it's from to ask about the email, along with other verification methods.
RELATED: What Is Phishing? [Types and Tips to Prevent]
Set Up Secure File-Sharing
Remote working doesn't halt the sharing of private documents and sensitive information. Setting up secure file-sharing platforms ensures that business continues to flow smoothly and securely.
Platforms such as OneDrive or ShareSync let you open and view your synced files directly from your phone and share files with co-workers and clients.
Keep in mind that if you have a Managed Service Provider, you may already have a secure file-sharing service bundled into your cyber security package, which will save you the cost of having to buy one of these platforms.
Business phones may also come with a feature called “Find Me Follow Me”, or twinning. With this feature, calls are forwarded from an employee's desk phone to their mobile phone.
If that employee doesn’t pick up after a few rings, instead of letting someone leave a voicemail on their mobile phone, which can mean that sensitive information is now stored on an employee's personal device, the call is re-routed back to that employee's desk phone so someone can leave a voicemail there instead.
Then, a transcript of the voicemail is emailed to that employee. This feature lets you control where your company's data is stored by ensuring that no voicemails that may contain sensitive data are left on an employee's personal device. If you have this feature, enable it before taking your office remote.
Institute a Company-Wide Protocol

While having a VPN and a password policy are great ways to protect your network while working remotely, sometimes the greatest potential network threat is a lack of open communication among your staff.
If an issue or threat pops up in your network, make sure that your staff understands the proper channels for communicating issues. In the event of a network breach or outage, your staff should know the emergency action plan that will be put into effect.
If you want to ensure that all staff are up-to-speed on cyber security do's and do not's, start by laying out a policy with a few basic tenants.
A main aspect of a cyber security policy should be the rules surrounding file-sharing. Especially if your company has to comply with data regulations such as HIPAA, you need to ensure that staff know how to share files with one another securely without putting your company's private data at risk.
Once you implement the points from the previous section, make sure that staff are trained on how to use the file-sharing software and can set up the "Find Me Follow Me" feature on their business phones.
While file-sharing procedures is a great first tenant to include in a cyber security protocol, instituting a password policy is another step you can take to ensure that data is safe and accounts aren't at risk of becoming breached.
Password policies educate your employees on how to create and maintain secure passwords. Basic aspects of a password policy could include points about making passphrases instead of passwords, not writing down passwords anywhere, and enabling two-factor authentication whenever possible.
Business Continuity and Disaster Recovery plans make your business poised to handle any network emergency that's thrown at it.
By creating a thorough plan and testing and updating it regularly, your business can be prepared to take swift and appropriate actions in the event of a natural disaster or network outage that interrupts business operations.
As a Managed Service Provider, we work with our customers to lay out the proper steps in a BCDR plan. We hope that this article answered your questions. For more cyber security related articles, check out our blog!
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

