CYBER SECURITY | 4.5 MIN READ
When you transition from a corporate office to a home office, the task of keeping your remote environment secure from cyber threats and malicious actors can seem complex. As a Managed Service Provider, we assist clients in.
cyber security solutions,
small business cyber security,
remote office
Read More
CYBER SECURITY | 6.5 MIN READ
Though a small business' margins are quite tight, that doesn't mean that cyber security should take a backseat. Poor cyber security can lead to ransomware attacks and other network issues that can have sizable costs to fix. .
small business cyber security,
small business cyber security solutions,
cyber security
Read More
CYBER SECURITY | 4.5 MIN READ
Cyber security is a complex and evolving process, which can make it difficult for businesses to efficiently and effectively protect their network from the countless cyber threats that exist. Security Operations Centers, also.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 5.5 MIN READ
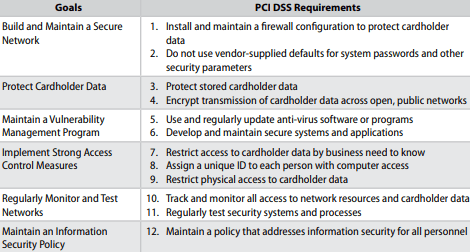
The finance, healthcare, and legal industries are frequently targeted for cyber attacks and are also subject to multiple data privacy regulations, which makes the task of effective and compliant cyber security difficult. As.
cyber security best practices,
cyber security solutions,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 5 MIN READ
Business Continuity and Disaster Recovery (BCDR) plans help organizations mitigate the risks associated with network downtime and interruptions to business operations. Keep reading to learn what a BCDR plan is, how your.
cybersecurity,
small business cyber security
Read More
REMOTE OFFICE | 9 MIN READ
Many companies who had their first remote trial run earlier this year amid the COVID-19 pandemic are now wondering if they should permanently keep their office remote. Keep reading to see all the factors a company should.
small business cyber security,
cyber security,
remote office
Read More
CYBER SECURITY | 4.5 MIN READ
Virtual Private Networks, known as VPN's, are a great asset to your business. By allowing your employees to access and share files on your network securely, you help mitigate the risk of data breaches. Keep reading to learn.
cyber security best practices,
cyber security solutions,
cybersecurity,
small business cyber security
Read More
CYBER SECURITY | 5 MIN READ
Expanding your company to multiple offices is an exciting development. When building new branches, you might not consider the necessary steps to set up your network to securely handle employees from multiple branches working.
cyber security best practices,
cyber security solutions,
cybersecurity,
small business cyber security
Read More
CYBER SECURITY | 9 MIN READ
Varying the passwords you use for everything from your email account to your company's HR database is a great first step at protecting your data, but what happens when you have so many passwords that you begin to lose track of.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 7 MIN READ
The healthcare industry must follow strict protocol to remain compliant with HIPAA. Because many organizations within the industry store private information like patient files and financial information, the industry as a whole.
cyber security solutions for small business,
small business cyber security,
cyber security
Read More
CYBER SECURITY | 8 MIN READ
The legal industry ranks among the healthcare and finance sectors as one of the most targeted industries for cyber attacks. The common thread that makes them attractive targets is the personal information that they store and.
small business cyber security,
small business cyber security solutions,
cyber security
Read More
CYBER SECURITY | 7.5 MIN READ
As a Managed Service Provider, our clients ask us about the benefits of cloud versus on-premise security all the time. Data security is becoming more and more crucial for businesses as cyber attacks are on the rise, which.
cyber security solutions for small business,
small business cyber security,
small business cyber security solutions,
cyber security
Read More
CYBER SECURITY | 4.5 MIN READ
The start of a new decade gives businesses a fresh start to strive towards achieving long-term goals. Businesses always think to set New Year's resolutions covering topics such as sales growth and business expansion..
cyber security best practices,
cybersecurity,
small business cyber security,
small business cyber security solutions
Read More
CYBER SECURITY | 4 MIN READ
Signing a Managed Services Provider contract is exciting, as it is the first step in better protecting your business from cyber threats. However, signing an MSP contract can mean reading over a lot of unfamiliar jargon. A term.
small business cyber security
Read More
CYBER SECURITY | 7.5 MIN READ
Running a business pulls your mind in a million different directions. When worrying about the usual business-critical tasks, taking time to focus on managing the security of your network can become a hassle. However, is your.
cyber security solutions for small business,
small business cyber security
Read More
CYBER SECURITY | 4.5 MIN READ
With 2020 around the corner, you're probably thinking about the approach of tax season or what gifts you'll be buying for the holidays. However, have you considered how you or your business will be affected by new cyber.
small business cyber security,
cyber security laws
Read More
CYBER SECURITY | 2.5 MIN READ
Windows 7 End of Life is coming early next year. Those who do not heed the warnings from Windows leave their networks at serious risk of being breached. Read on to find out what Windows 7 End of Life is, the risks.
small business cyber security
Read More
CYBER SECURITY | 5 MIN READ
While we don't have flying cars yet, society has advanced to the point that many other aspects of our lives are tied to technology. One way that our lives are inextricably tied to it is through the storing of our personal.
IT Solutions,
cyber security solutions for small business,
small business cyber security,
small business cyber security solutions
Read More