
PHISHING | 4 MIN READ
Have you ever received a phone call or email that seemed a little suspicious?Maybe the person or company contacting you seemed fake, or they seemed persistent about trying to get your personal information? Those may have been spam or phishing attempts. Spam and phishing are two related concepts that are easy to confuse. Keep reading to learn the difference between the two as well as how you can avoid falling for a phishing scam.
Not enough time? Jump to:
How to Prevent Phishing Attacks
What is Spam?

Spam is unsolicited junk email that is sent to mass numbers of people. Spam is usually sent with a harmless intent, for instance to sell you on a product or service.
Many spam emails do not contain malware or other harmful attachments that could wreak havoc on your computer. Think of these emails as a simple nuisance that many email providers usually block or automatically move to a Junk email folder.
However, spam is also an umbrella term that encompasses other forms of mass junk communication, such as phishing and advertising.
What is Phishing?

Phishing, a play on the word "fishing", is a cyber attack that's a form of social engineering.
It involves attempts to gain access to a victim's personal accounts or capture their sensitive data by tricking them into revealing passwords or personal information. The most common form of phishing takes place over email.
Phishing attacks aim to obtain your personal information through fraudulent means. For instance, you could receive an email appearing to be from a non-profit asking for donations, or a phone call from your bank demanding your social security number.
What are the Different Types of Phishing?
Email is by far the most common type of phishing attack. It is easy to carry out and reproduce on a massive scale with a simple click of a mouse.
Phone
Phone calls are about half as popular as email. For a phone phishing attack to be carried out successfully, the person calling needs enough personal information to sound convincing to the target (you). Phone calls are also harder to trace back to the attacker, but do take more time and effort.
In recent history, a popular phishing attack was carried out by people posing as an IRS agent on the phone, threatening to garnish wages or throw people in jail if they didn't settle there tax dispute over the phone.
Mail scams are not as common because they can be the most costly to implement. These scams are typically associated with a large bill to be paid, which is why it is most common as a healthcare scam.
RELATED: What is Phishing? [Types and Tips to Prevent]
What's the Difference?
While spam is usually harmless, phishing has malicious intent. While spam emails or calls usually try to sell you on a product or service, phishing scams attempt to obtain your personal information to carry out fraud or cyber attacks.
Spam content is also an umbrella term under which phishing falls. So, in a way, phishing is a type of spam, albeit a type with malicious intent.
How to Prevent Phishing Attacks
Email and phone providers realize that spam is a nuisance to their customers, which is why many have built-in settings to detect spam and alert you about an incoming spam message.
However, since phishing is so nuanced, many email providers don't have advanced enough filters to capture phishing attempts.
Luckily, most phishing attempts can be thwarted by taking a few simple steps. Besides paying attention to the warning signs previously listed, take a few actions when you see suspicious emails.
Recognize the Signs
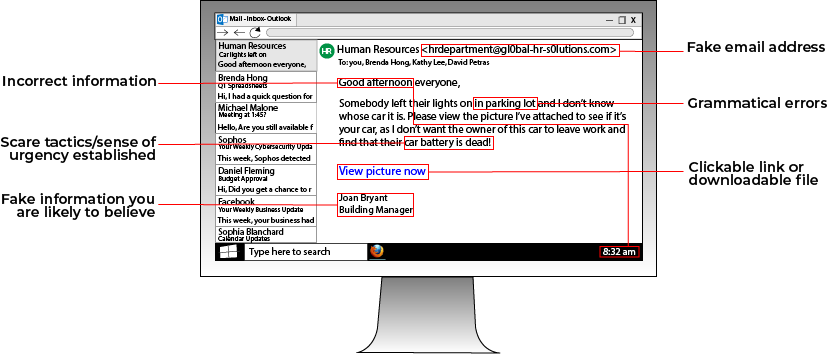
The most popular type of phishing attack takes place over email. Looking out for the above warning signs in a phishing email can stop an attack in its place.
In general, if an email supposedly coming from a bank or government institution asks you to click a link or immediately provide personal information over the phone, it may be a phishing attempt.
These types of institutions know that criminals love to pose as them, which is why they try to avoid business practices that lend legitimacy to criminal efforts.
If an email has just one of these warning signs, that may not automatically mean that the email is a phishing attempt. However, be sure to look at your emails from a big-picture viewpoint to figure out the intent behind the message.
Google It
If you think a phone call or email may be a phishing attempt, consider Googling some of the information in it, such as the company, phone number, or email address.
This can lead you to forums and reports from victims and show you if the company or person contacting you is fraudulent. A great website to reference is usa.gov and its list of common types of fraud.
Don't Download or Click on Suspicious Material
As a good rule of thumb to avoid falling for phishing emails, never download an attachment or click a link from an email, especially an unknown address, unless you requested something from the sender.
If you really think the email may be safe and want to test out a link, try finding the attached page yourself on Google first.
For instance, if you receive an email claiming to be from your bank asking you to click a link and enter information, try to find that same page yourself by visiting the bank's website without clicking on the link.
If your bank's website doesn't have that page and they don't know what you're talking about when you call them, then the email may be a phishing attempt.
Enable Email Filtering
Email filtering software analyzes incoming emails for red flags that signal spam/phishing content and automatically moves those emails to a separate folder.
Most major email providers have spam filters built in that move questionable emails to a "Junk" or "Spam" folder. Sometimes, these folders have a setting enabled that automatically deletes all emails in this folder after a specified period.
However, there are platforms whose services can be used to monitor for and flag phishing emails. These filters add an extra layer to your email security than just having spam filters enabled.
This software also typically comes with more general web filters that can be used to prevent you from visiting websites known to contain malware.
If you're a business, web filters can be used to boost employee productivity and better protect your network. Web filters can be used to block or warn employees attempting to visit malware-laden websites, or restrict traffic to websites that are common distractions such as social media platforms.
RELATED: What is Email Filtering and How Does It Work?
Knowing the difference between spam and phishing can mean the difference between clicking on a harmless promotional email and a malware-laden email designed to give a hacker access to your private documents.
As a managed IT services provider, our experience talking to and helping customers and prospects who have fallen for phishing attempts has granted us knowledge that we hope we can pass onto you.
We hope this article answered your questions. For more cyber security-related topics, follow our blog!
Posted by
Tech Support

