
PHISHING | 4.5 MIN READ
Criminals will take advantage of any new and unfamiliar situation to steal people's personal information and scam them out of money. The COVID-19 pandemic has provided criminals with a wealth of new opportunities to steal from hardworking citizens and small business owners. Keep reading to learn some of the top phishing schemes of 2020 and how you can avoid becoming a victim.
Not enough time? Jump to:
Phishing scams can lead to your personal information being published on the dark web. Understanding evolving dark web trends is crucial to preventing this.
Fill out the form linked here to get access to our exclusive State of the Dark Web report where you'll learn:
- 4 fast facts about the dark web
- 4 key takeaways and trends
- Two quick tips on how businesses can keep their sensitive information off the dark web
What is Phishing?

Phishing, a play on the word "fishing", is a cyber attack that's a form of social engineering.
Phishing attacks involve tricking a victim into revealing passwords and personal information or handing over money. The most common form of phishing takes place over email.
Criminals could trick an individual by posing as a legitimate business or government agency. For instance, you could receive an email appearing to be from a non-profit asking for donations, or a phone call from your bank demanding your social security number.
If you fall victim to a phishing attack, the consequences can be grave. Your personal information, ranging from credit card numbers to Social Security numbers, can be taken, which puts you at risk of experiencing fraud or identity theft.
If you click on a malware-laden link in a phishing email, ransomware can be downloaded to your computer, which means that your personal documents can be held for ransom.
Businesses whose employees fall for a phishing attack can later experience a ransomware attack, which can put them at risk of multiple penalties for data privacy violations.
What are the Different Types of Phishing?
Email is by far the most common type of phishing attack. These kinds of attacks typically have a link or attachment that, when downloaded, will install malware or ransomware onto your computer.
If malware or ransomware is loaded onto your computer, a hacker can access your private documents, steal your data, and hold it for ransom. They can also use personal information such as credit card and Social Security numbers to commit fraud.
Phone
Phone calls are the second most popular type of phishing attack. Criminals will sometimes research victims beforehand so they have enough information, for instance your children's names, in order to sound convincing on the phone.
A popular example of a phone-based phishing attack was when criminals posing as IRS agents threatened to garnish wages or throw people in jail if they didn't settle their tax dispute over the phone.
Mail scams are not as common because they can be the most costly to implement. However, that does not mean that they don't work.
When an individual is targeted with one of these attacks, one of the most common organizations that criminals pose as are healthcare organizations. These criminals will pose as hospitals, for instance, that are demanding repayment of a large bill or else a collections agency will be contacted.
The elderly in particular can be at risk for being targeted because they are more likely to have high healthcare bills, which makes them susceptible to believing these scams. Additionally, elderly people may be less likely to recognize the signs of a scam.
RELATED: What is Phishing? [Types and Tips to Prevent]
Coronavirus

The CDC has warned citizens about a phishing scam involving criminals who make calls appearing to come from the CDC. In these calls, they may ask for donations.
At least one scam is pretending to send emails from the CDC with attached links claiming to be infection prevention measures or information about a COVID-19 vaccine. In reality, these emails usually contain links to malware that can wreak havoc on computers and open the door for ransomware to enter and hack one's device.
Malware-laden emails have been used to take over healthcare organizations' networks and steal private information.
Coronavirus-related phishing scams have even taken place over text. Text messages appearing to come from the US Department of Health and Human Services send links to register for "mandatory COVID-19 testing". Texts can also urge recipients to complete the census or fill out an online form to receive a stimulus check.
In reality, these links download malware onto one's device, which can open you up to identity theft and fraud.
Stimulus Check/Small Business Loan

The US Small Business Administration has advised business owners to be cautious when applying for small business relief loans under the CARES Act.
Criminals posing as federal workers have been contacting business owners asking for additional personal information in order to approve an application for relief loans.
The Better Business Bureau has also warned citizens about phishing scams related to stimulus checks. Criminals will contact people asking them to provide additional personal information in order to send out benefit payments.
Keep in mind that when it comes to government-based payments or official government communication, these offices will never ask for personal information over the phone or through email, especially if it requires you to immediately pay money in order to receive something from them or avoid a penalty.
When it comes to the stimulus checks, since this money was sent automatically through the government, citizens especially do not need to provide additional personal information over the phone or through email in order to receive their check.
Presidential Election

With the presidential election quickly approaching, criminals are taking advantage of the confusion surrounding voting this year to carry out scams and phishing attacks.
Con artists have been posing as political volunteers attempting to register voters or solicit donations over the phone. In these scams, the "volunteer" will ask for donations to a candidate/political party with a credit card number, or will ask for personal information such as a Social Security Number in order to fill out a voter registration form.
In reality, voter registration over the phone is not permitted in the US as this creates opportunities for criminals. If you receive a phone call like this, assume that it's fraudulent.
How to Avoid Phishing Schemes
Phishing is so nuanced that many email providers don't have advanced enough filters to thwart attacks. Since email-based phishing attacks are the most common, we thought we would share some simple steps you can take to avoid becoming a victim.
Recognize the Signs
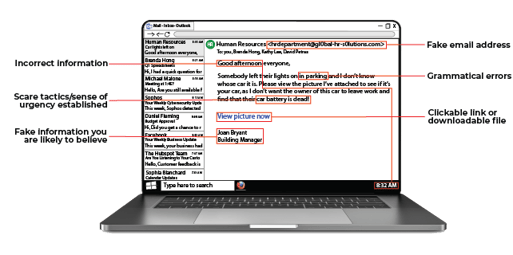
The most popular type of phishing attack takes place over email. Looking out for the above warning signs in a phishing email can stop an attack in its place.
In general, if an email supposedly coming from a bank or government institution asks you to click a link or immediately provide personal information over the phone, it may be a phishing attempt.
These types of institutions know that criminals love to pose as them, which is why they try to avoid business practices that lend legitimacy to criminal efforts.
If an email has just one of these warning signs, that may not automatically mean that the email is a phishing attempt. However, be sure to look at your emails from a big-picture viewpoint to figure out the intent behind the message.
Don't Download or Click on Suspicious Material
As a good rule of thumb to avoid falling for phishing emails, never download an attachment or click a link from an email, especially an unknown address, unless you requested something from the sender.
If you really think the email may be safe and want to test out a link, try finding the attached page yourself on Google first.
For instance, if you receive an email claiming to be from your bank asking you to click a link and enter information, try to find that same page yourself by visiting the bank's website without clicking on the link.
If your bank's website doesn't have that page and they don't know what you're talking about when you call them, then the email may be a phishing attempt.
Google It
If you think a phone call or email may be a phishing attempt, consider Googling some of the information in it, such as the company, phone number, or email address.
This can lead you to forums and reports from victims and show you if the company or person contacting you is fraudulent. A great website to reference is usa.gov and its list of common types of fraud.
Enable Email Filtering
Email filtering software analyzes incoming emails for red flags that signal spam/phishing content and automatically moves those emails to a separate folder.
Most major email providers have spam filters built in that move questionable emails to a "Junk" or "Spam" folder. Sometimes, these folders have a setting enabled that automatically deletes all emails in this folder after a specified period.
However, there are platforms whose services can be used to monitor for and flag phishing emails. These filters add an extra layer to your email security than just having spam filters enabled.
This software also typically comes with more general web filters that can be used to prevent you from visiting websites known to contain malware.
If you're a business, web filters can be used to boost employee productivity and better protect your network. Web filters can be used to block or warn employees attempting to visit malware-laden websites, or restrict traffic to websites that are common distractions such as social media platforms.
RELATED: What is Email Filtering and How Does It Work?
Criminals' tactics for scamming and defrauding us are constantly evolving. As a managed service provider, we aim to help our customers and their networks stay one step ahead of these con artists.
We hope that this article was informative and helped teach you how to avoid becoming a victim of a phishing attack. For more cyber security-related content, follow our blog!
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

