
PHISHING TESTS | 6 MIN READ
If you're looking for information on phishing tests, including what is a phishing test, then you've come to the right place. This article will cover everything you want to know about phishing tests, including what you can expect when implementing a phishing test, the different options you can choose for your phishing test, and some of the different providers of phishing tests.
What is a phishing test?
A phishing test is leveraged to simulate a real-life example of a phishing scam. These tests are traditionally created with software and implemented by an organization's IT team (or acting team) to train their users on the varieties and dangers of online phishing via email. The goal of a phishing test is to educate users of phishing dangers and to reduce the risk of hackers gaining access to sensitive information.
OFFER: Get a Complimentary Phishing Test Trial, Today
Not a lot of time? Skip to what you need:
What is phishing?
Phishing is a form of social engineering involving the use of bait tactics to trick users into giving away personal and/or sensitive information via email. The first known cases of phishing attacks were discovered as early as January of 1996, though it is possible they began before that.
Since that time, phishing scams have become increasingly more sophisticated, and hackers employ a variety of modern and custom tactics to trick users into divulging sensitive information like usernames and passwords.
Usernames and passwords from accounts as benign as Facebook have become valuable due to the lazy factor of most users. Many individuals will use the same email/username and password for a variety of logins. What seems like just a compromised social media login could quickly become something much more insidious.
Below is a real example of a phishing email that I received earlier this year:
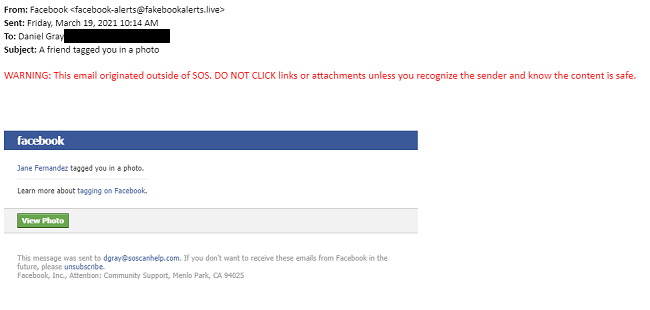
Now, I am usually very cautious about phishing. After all, I work for an IT company and we do phishing tests all the time to educate our employees.
But I work in the marketing department, and as a result, I work with our social media pages. Facebook happens to be one of them, so I went ahead and clicked the green button. After all, I wanted to know why someone was tagging our company in a picture (or so I thought).
Luckily, my ADD kicked in and someone stopped by my office and distracted me before I could go any further. The button had taken me to an identical login screen for Facebook - but it was fake.
I never put my login information into those fields and eventually forgot that I was going to login altogether...
...until I remembered later.
Sometime that afternoon, I remembered that I had not logged into my Facebook account to see who had tagged me. Then it dawned on me; my work email is not associated with my personal Facebook page and I have never been sent a notification for our company Facebook page in the past.
I went back to look at the email again, and this is what I discovered:
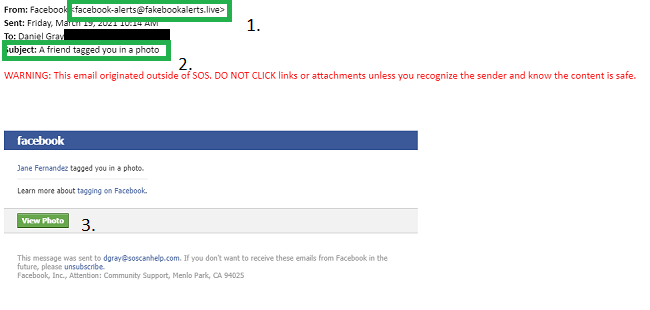 Upon further inspection, I discovered a glaring red flag. The sender address (1) read "@facebookalerts.live." That right there was all of the evidence I needed to know this was "phishy." Facebook is a billion-dollar company and would never use a ".live" address to send official correspondence.
Upon further inspection, I discovered a glaring red flag. The sender address (1) read "@facebookalerts.live." That right there was all of the evidence I needed to know this was "phishy." Facebook is a billion-dollar company and would never use a ".live" address to send official correspondence.
Next, I looked at the Subject line (2). It read, "A friend tagged you in a photo." If this had been a legitimate Facebook message to me personally, it would have been sent to my personal email. Otherwise, why was Facebook calling one of our business' followers a friend?
Finally, I just want to point out the quality of this phishing attempt. The green button at the bottom (3) looks like it was lifted straight off of Facebook (and it probably was). It tricked me into believing it.
The Silver Lining
Fortunately for me, this was a phishing test conducted by my company through our software provided by our partners at Sophos™. I was so thankful for the distracting co-worker from earlier, though, because had I input my information into that login screen, I would have been "sentenced" to automated training to learn from my mistake.
RELATED: What is Phishing & How Are Hackers Using It
RELATED: How to Spot a Phishing Attack
How Do Phishing Tests Work?
The story above is very similar to a typical phishing test. The phishing tests that we offer include over 500 phishing examples written in 10 different languages, so there is quite a variety to choose from.
Our IT department will even create our own versions from time to time that can be very specific. For instance, there was a period of time where I helped make sure that the break room refrigerator stayed clean (people liked to bring food and forget about it).
I received an email from a co-worker, addressed to the entire company, that stated that she had cleaned out the refrigerator and needed someone to claim an item that was found within it. She directed everyone to click the image that was attached to the email to see if it was their item.
Pretty clever phishing tactic if you ask me. And what company doesn't have an email sent every now and then about a refrigerator cleanout?
Needless to say, people fell for the test and were required to do mandatory phishing training. Our training is set up so that if you click the link, it automatically redirects you and declares that you have failed a phishing test.
The training can be completed immediately or later and includes a presentation on how to spot a phishing email. At the presentation's conclusion, they are administered a phishing quiz that must be passed in order to avoid doing the training again.
It's very effective and makes employees think twice before clicking an attachment or link in an email.
We set these tests up by:
- Importing all of the companies contacts into the phishing test's database
- Selecting or creating the phishing test we want to administer
- Selecting the employees we want to target for the test
Are there other phishing test options available?
Absolutely! There are paid-for and free phishing test options available, but I have to caution you, you get what you pay for in many cases.
The cost of a phishing test is pretty minimal but decreases further the more "seats" you purchase. That being said, if you feel you cannot afford to spend money on a phishing test subscription, it is better to use the free versions versus nothing at all.
"4,000 businesses are breached every day and 91% of them begin with a phishing attack."
Sophos, Mimecast, and KnowBe4 are all examples of companies that have phishing tests available for purchase (and a free 30-day trial) but do your research.
RELATED: Sophos vs Symantec Endpoint
A Word About Managed IT Services
Phishing tests are great and significantly reduce the risk of being hacked through employee error (the biggest hacking threat of all), but mistakes still happen.
It is incredibly important to have a strong backup and disaster recovery strategy, and rely on in-house or a third-party managed IT service provider for those instances where a cyber criminal does make it through your defenses.
If you need assistance with your network security planning, reach out to Standard Office Systems today for a consultation.
It could be the best decision you've made for your company all year.
Posted by Daniel Gray

Daniel has a passion for educating and helping people and has spent over a decade in the education and office technology industries. He has a Bachelor's in Education from the University of West Georgia and an MBA from the University of Georgia. Daniel has been the lead writer at SOS since 2017 and specializes in managed IT services, copiers and printers, and business phone systems. He lives in Atlanta and has a goofy greyhound named Ticker.

