
CYBER SECURITY | 6 MIN READ
Lack of privacy. Unauthorized usage of your devices. Data breaches. Loss of personal information. These are just a few of the potential consequences of cryptojacking. It poses serious threats to you and your business, so a clear understanding of it is crucial. Read more to learn what cryptojacking is, how it poses a threat, and how you can protect your network.
Not enough time? Jump to:
How Cryptojacking Poses a Threat
How You Can Better Protect Your Network
What is Cryptojacking?
Cryptojacking is the unauthorized use of a computer or other device by cyber-criminals to "mine" cryptocurrency. Usually, victims don't even notice that their computer is being taken advantage of.
Cryptocurrency, a form of digital currency, can be “mined” on a computer by using special programs to solve complex and encrypted math equations. Once the equation is solved, a user gains a piece of the currency.
How Does Cryptojacking Work?
To mine cryptocurrency on a victim's computer, a cyber-criminal must place a piece of code on the victim's computer. The code then starts solving the equations and sending results back to the hacker's server.

To place the code on a victim's computer, a cyber-criminal uses one of a few tactics. Usually, a phishing scheme is used. When a victim opens a phishing email, all they see is a harmless email with a link or attachment. Upon clicking the link or attachment, the crypto-mining code is downloaded. The code then starts to mine cryptocurrency, working in the background to avoid detection.
Another method of placing crypto-mining code is through the use of a website. Hackers embed the code within the website itself or in an ad on the site. Then, when a victim either visits the website or clicks the ad, the code automatically executes, which allows it to work in the background without being stored on the victim's computer.
Why Use Other People's Computers for Crypto-Mining?
Using other people's computers to mine cryptocurrency is faster and cheaper. For instance, if you hack 100 computers, you can have a whole fleet working and sending money to you. Mining also takes up resources like electricity to power the computers, which can add up fast if you're trying to run an entire operation from your own house.
Why Cryptojacking is a Lucrative Operation
Since cryptocurrency is a relatively new invention, most businesses do not accept it as a valid form of payment. One of the few places that your cryptocurrency is guaranteed to work is on the dark web.
Though some hackers mine cryptocurrency to keep it for a later date when it's worth more or has more widespread spending power, many use the cryptocurrency they mine to make purchases on the dark web. Purchases could range from drugs to lists of account passwords to much more.
How Cryptojacking Poses a Threat
Besides the annoying side effects of having your computer slowed down and used without your permission, cryptojacking is dangerous because it could lead to a full-on network hack.
Once a hacker knows that you fell for a phishing scheme, they could send you another phishing email, this time with a link to malware that infects your network, allowing them to now steal all your personal files and hold them for ransom.
If you are an organization that must remain compliant with data regulations like HIPAA, data breaches can cause you to be punished for non-compliance or even sued in some cases.
RELATED: Can Businesses Be Sued for Data Breaches?
How to Detect and Prevent Cryptojacking
Even though cryptojacking can happen right under your nose, there are a few ways to prevent and stop it. For instance, if you know the signs of a phishing scheme, you can avoid clicking any malicious links.
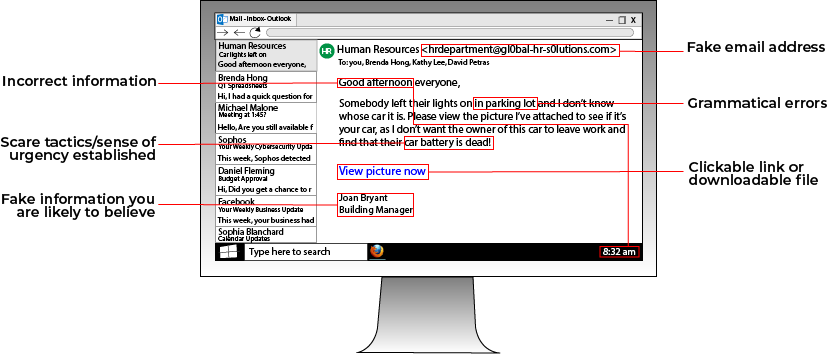
If the code is already on your computer, noticing a few warning signs can help you detect its presence. Pay attention to any unusually high processor usage on your device, sluggish or unusually slow response times, and excessive overheating of your device.
If you can trace the code back to a website you visited recently, block and report it.
How You Can Better Protect Your Network
If all this talk about cryptojacking has you worried that your network isn't safe from hackers, we have you covered with a few tips to strengthen your cyber security today.
Institute a Password Policy

Weak passwords are one of the easiest ways that a hacker can break into your network. Instituting password policies, whether it's for personal or business use, can keep your accounts more secure.
A main focus of any password policy should be to limit how much you write down your passwords, whether they're on a sticky note, an Excel spreadsheet, or in the Notes app on your phone.
If you write account passwords down on your phone, all it takes is your phone being stolen or your iCloud account being hacked for somebody to have the logins to accounts that contain sensitive information such as your credit card number.
If you have too many passwords to remember, consider a secure password-storing program such as MyGlue. These programs store all your passwords in one highly encrypted and secure place, allowing you to log into your accounts with ease and peace of mind.
To maintain strong passwords, consider creating passwords that don't use easy-to-find information such as birthdays or your children's names. When creating a password, make sure it's long and complex.
Additionally, install two-factor authentication on your devices if possible, seeing as it's a widely used secure method of protecting accounts.
RELATED: Cyber Security Awareness Training for Employees [Tips]
Stay Current with Software Updates and Security Patches
Many people forget or push off updating their anti-virus software or upgrading their firewall. While it's annoying to wait for your device to finish updating, these updates are crucial for patching any gaps in your security.
Every day that you wait to update your cyber security infrastructure after updates are released leaves you more vulnerable to data breaches. If you are able to, enable auto-updates on all security software and schedule any updates for late at night when you're not using your computer.
Auto-updates ensure that your software is constantly running at the latest version, which decreases the odds of a hacker finding and exploiting security gaps.
Consider Managed IT Services

If you are a business, you might not have the time to institute all these changes, especially if you only have an in-house IT manager or another employee handling your cyber security.
Managed IT services can put all of the above suggestions and more into action. Managed IT services layers your cyber security infrastructure with the latest hardware and software, employing a team of IT experts to address any issues that pop up.
MSP's can conduct phishing tests to find employees who fall for phishing traps, and then educate those employees on how to recognize and avoid phishing attacks. To take phishing prevention a step further, a managed services provider can even enable email filtering services to stop phishing emails in their tracks.
In the event of a data breach or network outage, MSP's can reduce downtime by quickly recovering data due to their use of frequent and secure backups.
Don't wait until you're the victim of a data breach to improve your cyber security. If you wait, you're already two steps behind.
RELATED: Cyber Security Solutions: 12 Best Practices for Businesses
Posted by Erica Kastner

Erica Kastner is a lead Marketing Specialist at Standard Office Systems as well as a University of Georgia graduate. She aims to use her passion for problem-solving to help businesses understand how to better leverage their network infrastructure.

