CYBER SECURITY | 5.5 MIN READ
The finance, healthcare, and legal industries are frequently targeted for cyber attacks and are also subject to multiple data privacy regulations, which makes the task of effective and compliant cyber security difficult. As an Atlanta-based Managed IT Services Provider, we help our clients secure their networks through proactive network monitoring and maintenance. We aim to use our expertise to arm our audience with the tools to have effective cyber security. Keep reading to learn about finance industry cyber security and learn a few tips to better secure your business' network.
Not enough time? Jump to:
How the Finance Industry is Vulnerable
Why Finance Industry Cyber Security is Important
How the Finance Industry is Vulnerable

Internal IT Processes are Lacking
The following statistics are based on recent surveys published by Deloitte, Clearswift, and the Ponemon Institute.
- As of 2020, businesses in the finance sector dedicate 0.48% of revenue and 11% of their IT budget to cyber security. Since this percentage comprises such a small portion of these business' budgets, this potentially create security gaps.
- From 2018-2020, survey respondents have identified "rapid IT changes and rising complexities" as their biggest cyber security challenge. Struggling to keep up with a constantly evolving cyber landscape can make it tough for businesses to effectively keep their network infrastructure updated.
- Increased implementation of remote work environments and online security processes mean that traditional network boundaries between companies and their customers, vendors, and partners are becoming more blurred, which can potentially create security gaps. This signals an increased need for a Zero Trust security models.
- Embedding cyber security into new products and channels remain the top two business security issues among those surveyed. This signals a need for proactive security updates to effectively protect the data these technologies contain.
- 70% of the surveyed financial institutes have experienced a security incident in the last 12 months, and employee failure to follow security protocols was identified as the leading cause of most of these incidents. While these business' networks may be secure, employee cyber security education should be a higher priority than it currently is.
- 56% of survey respondents reported that their organization effectively detected cyber attacks but only 31% said they were effective in preventing attacks. This statistic points to a larger issue surrounding a lack of proactive cyber security procedures.
The Cost and Frequency of Cyber Attacks are Increasing
The following statistics are based on recent reports and surveys published by Accenture, the Boston Consulting Group, and the IBM X-Force Threat Intelligence Index.
- In the financial sector from 2017-2018, the average number of cyber breaches jumped by 13%. As the finance sector becomes more frequently targeted for cyber attacks, increased cyber security spending will become more key.
- Within the financial sector, the average annual cost of cyber crime per company was $18.5 million. The cost of mitigating cyber crimes can potentially cause businesses to close permanently, which is why proactive cyber attack prevention should be a top priority.
- Banking and financial institutes are 300 times more likely to be at risk of a cyber attack than other companies. This is largely because of the valuable sensitive data that their networks hold, which is why effective holistic network security measures should be implemented and regularly updated.
- The financial services sector has been the most attacked industry for the past 4 years, accounting for nearly 20% of the cyber attacks across all verticals in 2018. Companies in this sector need to ramp up their security efforts if they wish to avoid becoming a part of this statistic.
RELATED: Top 6 Cyber Security Tips for Businesses [2021]
Why Finance Industry Cyber Security is Important

As data privacy becomes more of a concern for consumers, more data privacy regulations have been passed to hold companies accountable for any data breaches that cause sensitive customer information to be accessed.
The finance industry is held accountable for data breaches through several data privacy regulations: the Sarbanes-Oxley Act (SOX), the Gramm-Leach-Bliley Act (GLBA), and the Payment Card Industry Data Security Standard (PCI DSS).
These regulations set standards for the protection of sensitive customer data, and also describe non-compliance penalties. These regulations motivate the finance industry to set robust access controls, automated data backups, and more in a coordinated effort to secure their data.
The Sarbanes-Oxley Act (SOX)
Sarbanes-Oxley is a regulation that establishes transparent requirements for the storage and management of corporate financial records.
Storage and management includes logging and auditing, including strict new rules for accountants, auditors, and corporate officers and more stringent recordkeeping requirements.
Key sections of Sarbanes-Oxley include:
- Certifications for financial reports
- Corporate responsibility
- Increased criminal punishment
- Accounting regulation
- New protections
Gramm-Leach-Bliley Act (GLBA)
The GLBA requires financial institutions to transparently explain their information-sharing practices to their customers, grant customers the right to opt-out of the sharing of their data, and put adequate measures in place to protect sensitive customer data.
This regulation also sets standards for the collection, safekeeping, and use of private financial information.
Payment Card Industry Data Security Standard (PCI DSS)
This industry standard was put together by major credit card providers to reduce credit card fraud. If you are a company who processes data from major credit card holders, you must follow this standard and continue to stay up-to-date with regulations.
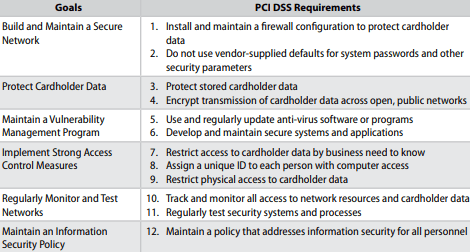
PCI DSS sets standards for institutions that store, process, or transmit cardholder data. This regulation aims to restrict cardholder information and data access to the minimal number of employees necessary, and implement administrative controls to track account activity.
The image below, taken from the PCI DSS official website, summarizes some of the main requirements.
Since the specifics of these regulations varies based on factors such as the type of business you own, visit this link to see what regulations you should follow based on the type of business you own.
RELATED: Can Businesses Be Sued for Data Breaches?
5 Cyber Security Tips

Internal Infrastructure Audit
To better secure your network and stay compliant with data privacy regulations, we recommend conducting a thorough audit of your network infrastructure quarterly to identify security gaps and build a roadmap to better network security.
This process, also known as a network assessment, should also aim to identify processes that are putting your business at risk of non-compliance with data privacy regulations. This can involve evaluating:
- Your data privacy architecture, which can include your backups, data breach notification processes, data erasure processes, and more
- Data audit trails
- Activity report logs, templates, and response records
If your business wishes to conduct a thorough network assessment and doesn't know where to start, a Managed Service Provider can help.
Conduct Dark Web Scans
Imagine what would happen if sensitive company files were uploaded to the dark web.
Hackers upload these files for sale on the dark web because they sometimes contain lucrative private information like credit card numbers. This can then lead to financial fraud, data breaches, and other negative financial consequences.
Dark web scan software can assist in preventing future data breaches by scanning the dark web to see what, if any, private company information is on it. For instance, the scan can find any employee email account credentials that have been published.
As a good rule of thumb, companies should conduct dark web scans annually so that any information that's found can show which security flaws need to be addressed.
As a Managed IT Services Provider, we make sure to conduct dark web scans for our clients so they can see what information is out there and adjust their cyber security plan accordingly.
Educate Employees About Cyber Security
Educating employees about cyber security starting from when they're hired helps to foster a company culture around the importance of cyber security and decrease the chances of new hires becoming an internal security threat.
Educational processes can be as simple as an educational pamphlet that the new hire has to read and take a test about during the first week of their employment, or password policies that standardize best practices when creating account logins.
Creating a monthly company cyber security newsletter can serve as an informative and engaging way to constantly educate your employees about the latest cyber security threats as well as serve as a way to share tips on staying safe online.
Another engaging way to see how educated your employees are about cyber security is to utilize penetration testing. Penetration testing is a fake phishing attack that aims to see which employees fall for the attack by clicking on fake links or downloading fake files.
If employees fall for these phishing attempts then you can send them through cyber security training, again. We recommend conducting this test quarterly.
Use Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) has emerged over the past few years as an alternative to VPN's. While VPN's are a great way to secure a network, issues have emerged surrounding latency, productivity hampering, scaling difficulties, and more.
The central premise of the Zero Trust belief is that organizations shouldn't automatically trust anything inside or outside their network until there is proof that they can. Furthermore, access should be granted on a "need-to-know", least privileged basis.
ZTNA protects against the potential security risks associated with automatically trusting that everything within one's network is safe. When organizations automatically trust programs and software, they potentially open themselves up to cyber breaches.
Though Zero Trust Network Access can be complex and takes a lot of work to implement, it is currently one of the leading industry security frameworks. ZTNA ensures that users can securely connect to private applications without placing them on the network or exposing those applications online.
There are four core tenets of Zero Trust Network Access that can be applied to an organization's network:
1. Separate application access from network access.
2. Only make outbound connections to ensure that unauthorized users cannot see network and application infrastructure.
3. Once users are authorized, only grant application access on a one-to-one basis. Authorized users shouldn't have full network access.
4. One's network should be de-emphasized and the Internet should become the new corporate network.
5 Steps to Build a Zero Trust Network Access Policy
1. Segment the Network
This step is arguably one of the most crucial in implementing an effective ZTNA policy.
Organizations should separate systems and devices based on which types of access they allow and what information they process. Based on these segmentations, one can then form the trust boundaries.
2. Strengthen Identity and Access Management
Identity and access management infrastructure needs to be strengthened when a ZTNA policy is built.
This can be accomplished by utilizing two-factor authentication and role-based security procedures, which ensure that users only have access to the platforms and applications they need to do their jobs.
3. Extend Least Privilege Policies to Your Firewall
A core tenet of Zero Trust Network Access is to not automatically trust anything within or outside of your network. This tenet can be followed by restricting access between networks through your firewall as much as possible.
This is similar to following a closed-door firewall approach, which we'll explain later in this article.
4. Add Application Context to Your Firewall
By adding application inspection technology to your firewall, you ensure that traffic passing in and out of your firewall is verified and safe.
This can mean, for instance, that your firewall checks to verify that outbound traffic corresponds to queries and isn't being abused by a hacker.
5. Implement a Security Information and Event Management (SIEM) Solution
SIEM solutions let IT managers parse through data collected from security events using a centralized view.
These solutions help companies quickly identify and remedy network threats that take place across systems, devices, and applications within one's network.
Consider Managed IT Services
Setting cyber security and data privacy compliance protocol can be complex, especially seeing as industry best practices shift to stay ahead of hackers and cyber criminals.
Businesses with little to no internal IT staff can benefit from using a third-party Managed Service Provider (MSP) to conduct a thorough network assessment, build and implement a roadmap to effective cyber security, and consistently monitor your network for cyber threats.
An MSP can implement the above cyber security protocol and more to secure sensitive data and keep your business compliant with data privacy regulations.
As a metro-Atlanta based Managed Service Provider, our diverse offering includes:
- Network monitoring− Consistent observation of all parts of your network ensures that any issues are swiftly identified and mitigated
- Cyber threat prevention and education− Layers of the latest technology neutralize threats while courses and phishing tests teach employees how to secure company data
- Data security− BCDR plan implementation and data privacy regulatory compliance ensure that data is backed up and data loss is minimized
- Network Operations Center− 24/7 assistance from a help desk with higher satisfaction ratings than Amazon and Ritz-Carlton customers
- Project management− Get assistance planning office expansions, moves, remote transitions, and more from qualified experts
RELATED: Who is a Good Fit for Managed IT Services?
Financial industry cyber security is a complex and evolving process that businesses need to increasingly be proactive about dedicating internal resources to.
We hope this article answered your questions. For more cyber security content, follow our blog!
Posted by Andre Schafer

Andre Schafer is a Technical Account Manager at Standard Office Systems. He has spent his entire career in the Office Technology and IT fields. For nearly 30 years, he has held various roles, including Technician, Trainer, Analyst, and Account Manager. Andre’s focus has always been to understand his customers' business needs to provide the appropriate technologies and services.

